Kubernetes has become the de facto standard for container orchestration, providing organizations the ability to efficiently manage containerized workloads at scale. However, securing Kubernetes environments remains a significant challenge. Misconfigurations and vulnerabilities can expose Kubernetes clusters, leading to compromised infrastructure, data breaches, and more.
To address these security risks, ARMO has released Kubescape 3.0, the latest version of the popular open source Kubernetes security platform. With its extensive capabilities, Kubescape 3.0 aims to revolutionize Kubernetes security for DevOps teams and our panel at Talent500 will help you know all you need about the topic.
Let’s begin:
An Overview of Kubescape
(Credits)
Kubescape serves as a Kubernetes-native security platform, providing DevOps and platform engineering teams the tooling to effectively secure their Kubernetes environments.
“Kubescape 3.0 demonstrates our commitment to furthering open source Kubernetes security for the community.” – Shauli Rozen, CEO of ARMO and founder of Kubescape
First launched in September 2021, Kubescape was originally created as an open source tool for validating Kubernetes cluster security configurations against industry standards like the NSA and MITRE ATT&CK frameworks. Since then, it has rapidly evolved into a comprehensive security solution designed specifically for Kubernetes.
The project joined the Cloud Native Computing Foundation (CNCF) in 2022 as a sandbox project, demonstrating its growing prominence in the cloud native security space.
What’s New in Kubescape 3.0
Kubescape 3.0 introduces over a dozen major new features and capabilities that aim to streamline Kubernetes security for DevOps teams, including:
In-Cluster Storage of Scan Results
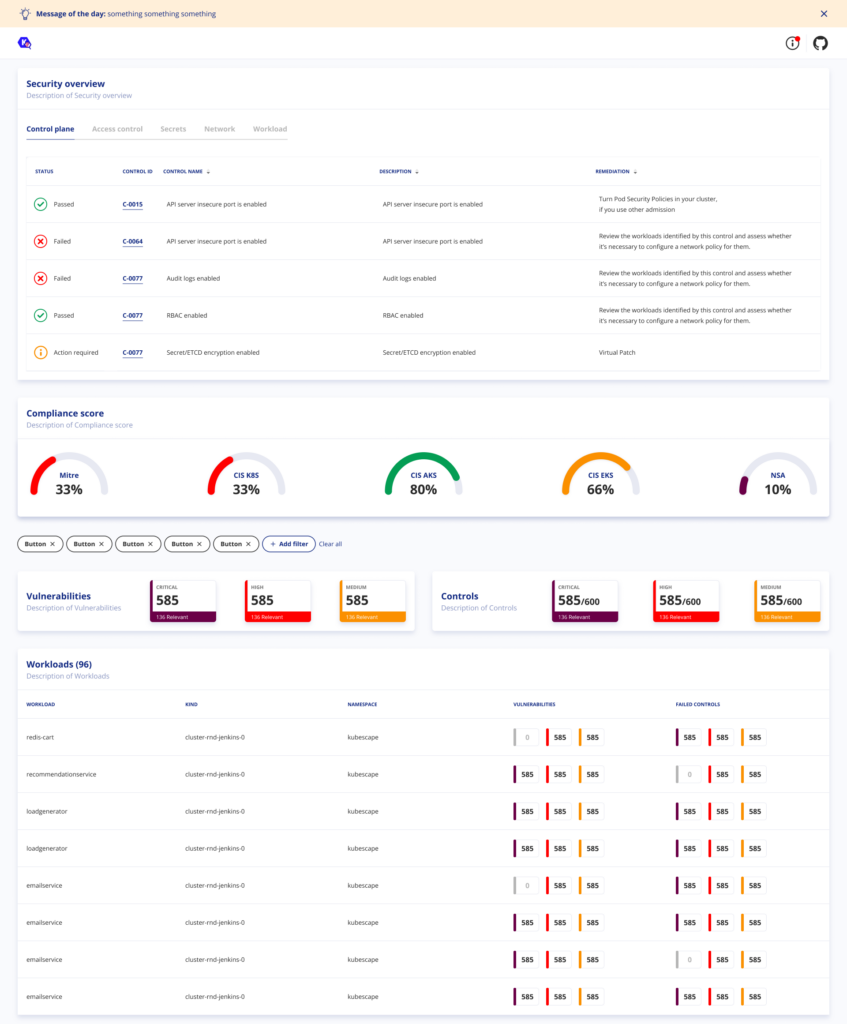
One of the most significant additions in Kubescape 3.0 is the ability to store compliance and vulnerability scan results directly within the Kubernetes cluster, through the Kubernetes API, rather than external storage solutions.
This in-cluster storage provides teams increased visibility into the security posture of their environments through Kubernetes resources. Scan results can be conveniently accessed like any other Kubernetes object, seamlessly integrating security data with existing workflows.
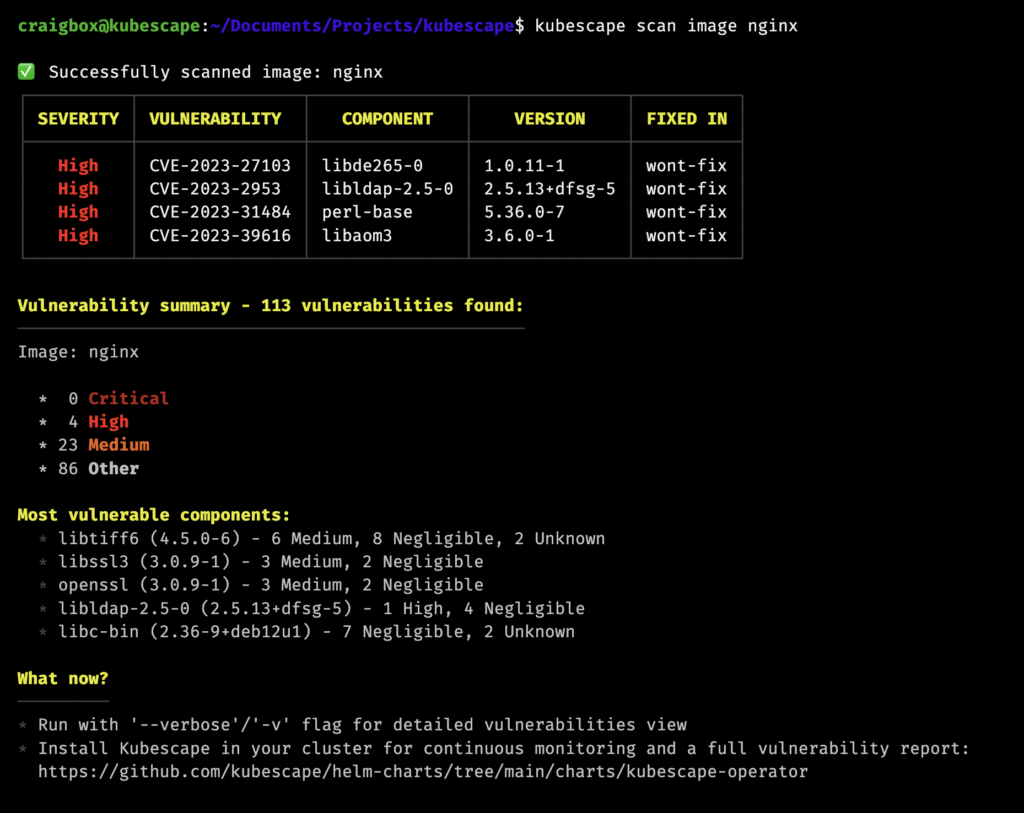
Command Line Interface (CLI) Vulnerability Scanning
The new Kubescape CLI enables image scanning, empowering teams to identify vulnerabilities early in the development process. Images can be checked for security flaws before deployment to production environments, shifting security left.
Cluster Image Vulnerability Reporting
Building on Kubescape’s image scanning capabilities, the platform can now generate aggregated vulnerability reports for all images running within a Kubernetes cluster. This cluster-level visibility enables organizations to prioritize patching based on risk, such as addressing critical container vulnerabilities first.
(Credits)
Overview Security Scanning
Kubescape 3.0 introduces a new overview security scan that serves as a baseline for cluster security. This scan identifies key risks and security issues that should be addressed to improve the overall security posture. Users can then establish risk acceptance rules to accommodate legitimate exceptions.
Improved Usability
The latest release focuses heavily on improving Kubescape’s usability. Enhancements include easier to interpret output, a streamlined Helm chart for simplified configuration, and better handling of certain edge cases with scans.
Monitoring and Observability
New Prometheus integrations allow teams to monitor the security posture of Kubernetes workloads, namespaces, and entire clusters over time. Alerting can also be configured to notify teams when critical security thresholds are exceeded.
External Data Storage
While Kubescape 3.0 adds in-cluster storage of scan results, the platform also now supports sending data to external third-party services for redundancy. This ensures security data remains available even if a cluster is compromised.
Several other capabilities round out the Kubescape 3.0 release, including highlighting high risk workloads, experimental image patching support, and improved output formatting.
Why Kubescape 3.0 Matters for Securing Kubernetes
Kubescape 3.0 represents a significant leap forward in simplifying Kubernetes security for DevOps teams through a set of enhancements targeted at core pain points.
Shift Security Left
By providing vulnerability scanning earlier in the development lifecycle, Kubescape enables a shift left approach to security – addressing flaws before they can reach production. This is significantly more efficient than waiting to handle vulnerabilities after the fact.
Improved Visibility
Storing scan results as Kubernetes objects grants teams increased visibility into the security posture of clusters. Security data is readily accessible rather than siloed in external systems.
Focus on What Matters
Capabilities like highlighting high risk workloads help teams focus security efforts where they will have the biggest impact. Kubescape enables pragmatic, risk-based prioritization.
Native Kubernetes Security
As a platform designed specifically for Kubernetes, Kubescape integrates seamlessly with native workflows through the Kubernetes API. It “speaks Kubernetes” to bridge the gap with security.
Automation-Enabled
Kubescape’s programmatic interfaces enable integration with CI/CD pipelines and infrastructure-as-code workflows, helping teams embed security earlier into DevOps automation.
Extensibility
The modular, open source nature of Kubescape allows organizations to customize the platform to meet their unique needs. Developers can also contribute features to expand the tooling.
Reduced Tool Sprawl
Consolidating various security capabilities into a unified Kubernetes-native platform helps reduce tool sprawl. Kubescape acts as a single pane of glass for Kubernetes security.
By combining these strengths into an easy-to-use open source solution, Kubescape 3.0 aims to make enterprise-grade Kubernetes security radically more accessible.
A Closer Look at Key Kubescape 3.0 Capabilities
Let’s explore some of the top new capabilities in Kubescape 3.0 to better understand how they aim to streamline Kubernetes security.
Scanning Images via CLI
Kubescape’s new command line interface provides DevOps engineers with the ability to easily scan container images for vulnerabilities without needing to deploy the agent to a cluster.
For example, developers can scan images directly from their CI/CD pipelines by invoking a simple command like:
| kubescape scan image –image nginx:latest –output json |
The scan will return a detailed list of vulnerabilities associated with that image. Teams can use this information to reject unsafe images before they enter production.
CLI scanning helps shift security left, catching issues extremely early in the process.
In-Cluster Storage of Results
Storing scan results directly within the Kubernetes cluster transforms how DevOps teams can interact with security data.
Compliance scan results are now represented as ConfigurationScanSummary API resources, while vulnerability reports map to VulnerabilityManifestSummary objects.
These Kubernetes-native resources integrate tightly with native tooling like kubectl and can trigger alerts or workflows.
For example, a team could configure a Prometheus monitor that fires whenever critical vulnerabilities in the cluster exceed a threshold, informing them to take action.
By adopting common Kubernetes patterns, Kubescape 3.0 aims to make security data more readily available and actionable.
Overview Security Scans
Kubescape’s new overview security scan acts as a baseline for cluster security by highlighting key risks and configuration issues that should be addressed.
For instance, the scan may report:
- 5 deployments with excessive privileges
- 13 images with critical vulnerabilities
- 2 insecure ingress rules
Teams can then drill into specifics through provided links and stabilize the weaknesses identified by the overview scan.
Additionally, users can create “risk acceptance” rules to accommodate known issues that don’t need remediation, suppressing them from future scan reports.
Together, these capabilities help teams establish an initial secure cluster configuration, laying the foundation for proactive security monitoring.
Real-World Examples
To better understand the value Kubescape 3.0 can provide, let’s walk through some examples of how DevOps teams might leverage the platform to enhance Kubernetes security.
Scanning Repositories in CI/CD Pipelines
A team is implementing continuous integration (CI) for their Kubernetes applications. Their GitHub repository is configured to run Kubescape image scans on all PRs and commits to main. If a vulnerability exceeds their risk threshold, the PR is blocked from merging.
This automatically shifts vulnerability identification left in the process, preventing unsafe images from entering the production environment altogether. The team can fix issues before they become downstream problems.
Generating Vulnerability Reports
A cluster operator needs an overview of the vulnerability landscape across all the applications in the production cluster. They execute a Kubescape vulnerability scan, storing the results directly in the cluster’s API as VulnerabilityManifestSummary objects.
The operator can now easily retrieve vulnerability data in the native Kubernetes tooling they use daily. They review the aggregated report and present key metrics around patching priority to application teams.
Establishing Security Baselines
A newly formed platform team inherits a sprawling Kubernetes environment without documentation. They run Kubescape’s overview security scan to establish an initial baseline, revealing numerous risky misconfigurations.
The team addresses the severe issues identified by the scan to bring the cluster to an acceptable security posture. They also create risk acceptances for known exceptions that don’t require remediation.
This provides a sound foundation they can continuously evaluate as they enhance the cluster’s security over time, preventing lapses as new applications are onboarded.
Monitoring Security Trends
A security-focused DevOps team wants data-driven insights into how cluster security evolves over time. They configure Kubescape scans to feed into their existing Prometheus and Grafana monitoring stack.
Customizable dashboards provide visibility into security trends across all namespaces, with the ability to drill down into specifics. The team sets up alerts to notify them of security regressions compared to their baselines.
With these observability capabilities, they can make data-informed decisions around Kubernetes security priorities and resourcing.
What’s Next for Kubescape?
The Kubescape project shows no signs of slowing down with its rapid iteration. The CNCF project has an aggressive roadmap planned.
Kubescape 3.1
The next release, Kubescape 3.1, is expected by the end of 2022. It will introduce a built-in web UI, improving usability through graphical visualization of security posture.
Kubescape 4.0
In Q2 2024, the milestone Kubescape 4.0 aims to further expand the platform into a full Kubernetes-native application protection platform, abbreviated KNAPP.
KNAPP will build on the existing framework with additional runtime security features designed specifically for Kubernetes environments. This could include capabilities like anomaly detection, behavioral analytics, and automated policy enforcement.
Get Started with Kubernetes-Native Security
Kubescape 3.0 provides a compelling vision into the future of Kubernetes security – one that tightly integrates with native tooling and workflows while remaining fully open source.
DevOps teams ready to embrace Kubernetes-native security can get started today by deploying Kubescape to their environments via the Helm chart. Commercial support options are also available through Kubescape’s enterprise platform for additional features, integrations, and capabilities.
As organizations accelerate cloud native adoption, properly securing Kubernetes environments grows increasingly crucial. By offering an elegant open source solution purpose-built for Kubernetes, Kubescape 3.0 aims to democratize enterprise-grade cloud native security for organizations of any size or maturity.
The CNCF project showcases the power of cloud native technologies to not just orchestrate applications, but also secure them. For DevOps teams struggling to effectively secure complex, distributed Kubernetes environments spread across public clouds and on-prem data centers, Kubescape delivers a compelling path forward.
That was amazing but here’s something even better: a better job with better take home salary, more benefits, and career advancement opportunities.
Sign up on Talent500 to get your next big DevOps job!






Add comment