DevOps is becoming synonymous to modern software development and it has helped developers deliver better software. It has also accelerated the rate of software delivery but left a glaring concern for modern enterprises: The rapid adoption of DevOps ideology and its high velocity of software delivery has left teams putting security on the backburner.
Lately, addressing security gaps within the DevOps workflow has become a key discussion point for many organizations. Hence, DevSecOps is becoming a mainstream term as more teams embed security organization into DevOps organization. In this article, we will help you learn about the top five security threats that you might be facing and the mitigation strategies to secure your interests. This article will serve as the foundation for your efforts of including security in your DevOps workflow and organizational DNA at large.
Let’s get started:
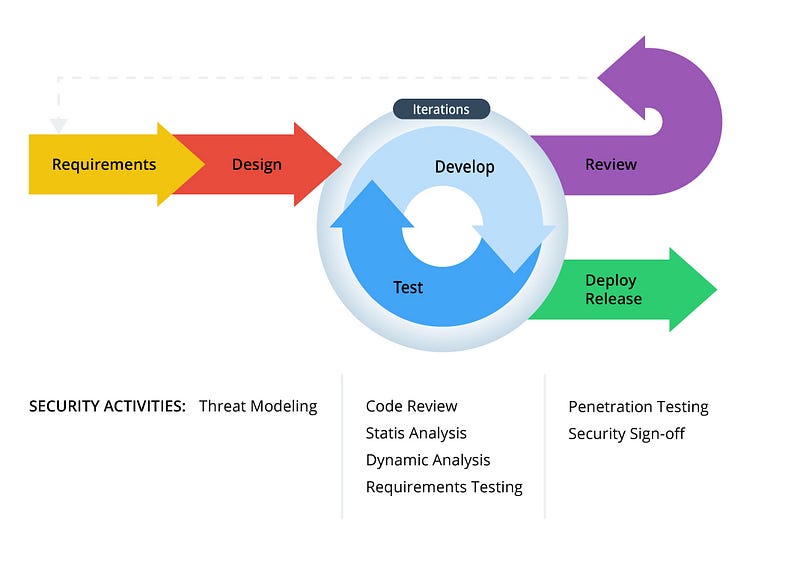
5 DevOps Security Threats To Address Immediately
In this section, I will walk you through five DevOps security concerns that you must address right away:
#1 Insecure Coding Practices
DevOps engineers might end up introducing vulnerabilities in their code through due to mistakes like these:
- Easy-to-guess passwords: Storing sensitive information with passwords that are simple or reused across different systems.
- Unfiltered user input: Not checking what users enter into forms or applications, which attackers might exploit.
- Outdated libraries: Using pre-written code (libraries) that have known security issues because they haven’t been updated.
Such mistakes of omission and commission, though unintentional, can create exploitable entry points for attackers, potentially leading to data breaches, system compromises, or the execution of malicious code within the application’s trusted boundaries.
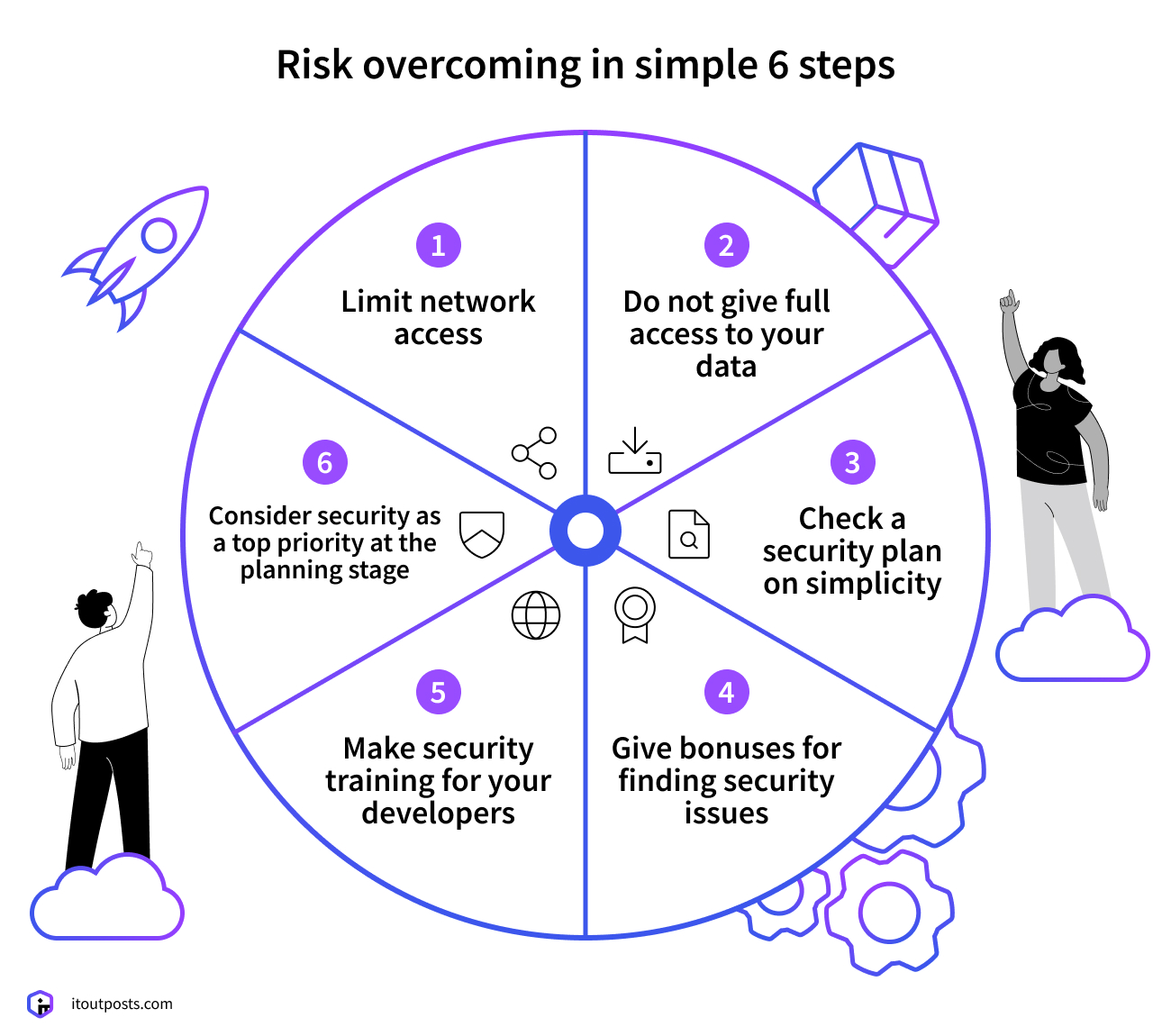
Mitigation Strategies
- As an organization, invest in comprehensive secure coding training programs to educate developers on the latest security best practices, emerging threat landscapes, and secure coding techniques specific to your organization’s technology stack.
- This will require you to work on your culture and ensure that security is ingrained into the development process right from the inception.
- You must integrate static application security testing (SAST) and dynamic application security testing (DAST) tools into the Continuous Integration/Continuous Delivery (CI/CD) pipeline. This will help detect vulnerabilities, coding flaws, and security weaknesses early in the development cycle. As a result, you will be able to timely remediate before the code is deployed to production environments.
- Next, you should create and monitor the enforcement of secure coding standards and guidelines that are tailored to your organization’s unique security requirements and technology stack. Conducting regular peer code reviews to ensure adherence to these standards and identify potential security issues before they are introduced into the codebase is an effective and efficient way of doing so.
To sum up, you must take proactive steps to make DevOps processes secure-by-design.
#2 Credential Mismanagement
Tool Sprawl is a rampant issue for DevOps teams due to added complexity, redundancy, and technological debt. It also acts as a huge cost center but the security hazards it causes is often overlooked.
DevOps pipelines heavily rely on a huge number of sensitive credentials like passwords, API keys, and SSH keys which are scattered across various tools and environments. It is not uncommon to lose track of how each of them are being utilized at different endpoints by respective DevOps team members. Result? These credentials are exposed to theft and attackers may gain unauthorized access to sensitive systems and data. This could result in cascading implications including legal trouble.
Mitigation Strategies
- Firstly, you must implement a centralized, secure vault solution for storing and managing secrets. You can choose from HashiCorp Vault, AWS Secrets Manager, Azure Key Vault or any other solution of your choice. They provide encryption, granular access controls, and comprehensive auditing capabilities to ensure the confidentiality and integrity of your organization’s secrets.
- Coming towards operating best practices, you must enforce strict secret rotation policies to minimize the potential impact of a compromised secret. You can also automate the process and make it more secure as it minimizes the attack window for compromised secrets.
- Adding to it, you can leverage secure retrieval mechanisms at runtime instead of hardcoding secrets into code/configuration files. This will help prevent sensitive information from getting inadvertently exposed through version control systems, misconfigurations, or accidental leaks.
- Last but not the least, access control and detailed audit trails should be a part and parcel of your DevOps strategy to create a security-first culture.
#3 Misconfigured Cloud Resources
DevOps teams often deploy applications and infrastructure across multiple cloud providers. While this may be deemed necessary, it increases the risk of misconfigurations that expose sensitive resources to potential attackers.
Some of the common misconfiguration examples include overly permissive access controls, insecure storage settings, and non-compliance with industry best practices/regulatory requirements. Again, this can lead to regulatory penalties as it enables attackers to carry out data breaches and compromise your cloud environments.
Mitigation Strategies
- Sit down with your team and create a plan for implementing infrastructure as code (IaC) principles. It will enable consistent and automated deployment of infrastructure resources. This will mitigate the risks caused by manual configuration errors and drift from established security baselines. However, the best advantage would be that your team would be able to treat the infrastructure as versionable, testable, and repeatable artifacts.
- I would also recommend implementing cloud security posture management (CSPM) tools like Prisma Cloud, Azure Security Center, or AWS Security Hub. They perform continuous scanning and remediation of misconfigurations across your cloud environments.
- Next on your list should be enforcing the principle of least privilege access for cloud resources, granting only the necessary permissions required for specific tasks/roles. These tools automate cloud security by finding and fixing misconfigurations.
One thing that you can start doing instantly is to implement change management for all cloud changes before deployment.
#4 Vulnerable Dependencies
Many DevOps teams resort to using open-source libraries, containers, and other third-party components into their applications. This is generally done to accelerate development and leverage existing functionality. It might be smart and harmless at thee first instance, but this is yet another way to help malicious actors exploit your trusted environments.
Mitigation Strategies
- To counter vulnerable dependencies, you must first implement software composition analysis (SCA) solutions. You can choose from options like Snyk, Black Duck, or OWASP Dependency-Check. They continuously scan applications and containers for vulnerable dependencies, making your job easier.
- However, I’d like to advise you to collaborate with vulnerability advisories as it takes a lot of thinking off your plate and helps you respond proactively in case of any security breach.
- I also recommend vetting and “whitelisting” trusted sources for third-party components as an immediate measure you can implement.
#5 Compromised CI/CD Pipelines
We all know that Continuous Integration/Continuous Deployment (CI/CD) pipelines are the backbone of DevOps workflows. But what if these very pipelines are compromised? In such scenarios, attackers can inject malicious code into your builds. Or, they may exfiltrate sensitive data from the pipeline. Under these circumstances, you can expect catastrophic damage to your applications, infrastructure, and the integrity of your software delivery processes.
Mitigation Strategies
- As a first measure to counter this threat, you must harden your CI/CD infrastructure with well-designed access controls and multi-factor authentication (MFA).
- Next, you must implement code signing and validation to ensure the integrity of builds and deployments. This is another instantly executable remedy for your DevOps team.
- Lastly, you may use SIEM tools to monitor pipeline activities and audit logs for suspicious behavior.
As a matter of fact, it’s best to create a clear separation of duties and enforce least privilege access in the CI/CD pipeline. These tactics will prevent attackers from moving laterally and escalating privileges during a compromise. As a rule of thumb, you must also develop backup and disaster recovery to protect your organization’s business continuity and your team’s software delivery processes.
Summing Up
Apart from the threats that we discussed, you must keep an eye on issues stemming from limited visibility and excessive access within DevOps. ELK or Splunk can come handy for monitoring across operations.
Having said that, there are two common factors that manifest as the threats we discussed:
- Rapid Development and Deployment Cycles
- Complexity in DevOps Environments
Getting carried away with these two results in security taking a backseat to speed and efficiency. If you manage to take care of this duo, your DevOps activities will turn out to be far more secure and mitigation strategies we discussed will become a natural part of your team’s approach to software.
Looking for a high TC remote job?
Sign up on Talent500 now!






Add comment