Flutter is an open-source mobile application development framework created by Google. It allows developers to build natively compiled mobile, web, and desktop applications from a single codebase. Flutter has gained popularity due to its fast development cycle, expressive and flexible UI, and good performance. However, as with any software, it is crucial to ensure that Flutter apps are secure. Here are some tips to consider when developing a secure Flutter app.
1.Store data safely.
Every app stores some private data in local storage like (accessToken, UserId, etc). Our app doesn’t need to request permission to view these files, and other apps can’t access the files. As an added security measure, when the user uninstalls an app, the device deletes all files that the app saved within the internal storage.
By default, All the info saved as plain text is not encrypted and can be read by anyone who has access to the device.
So the best practice is to encrypt the saved user data. There is a flutter plugin named flutter_secure_storage to store data in secure storage, Keychain is used for iOS and AES encryption is used for Android. AES secret key is encrypted with RSA and RSA key is stored in KeyStore.
2.Enable Local Authentication.
This feature is very useful if you have payment or subscription functionality. Suppose the user’s phone is lost or stolen and it has payment and bank account information in it. In order to prevent a third user from accessing your app, you should use biometric authentication as it provides an extra layer of authentication after a screen lock. When users want to open your app, ask for either a PIN/password/pattern or a biometric credential, such as face recognition or fingerprint recognition.
For biometric authentication, you can use local_auth package.
3.Secure the Backend.
Always use HTTPS over HTPP. HTTP is strongly not recommended. A secure network connection between mobile apps and servers is a prerequisite to ensure the protection of apps. Using a Transport Secure Layer (TSL) facilitates the secure exchange of information.
4.Permission
To prevent your app from acquiring unnecessary permissions contained in a plugin, it is advisable to only request the specific permissions required. By doing so, your app can access native APIs and hardware through the granted permissions.. Using this hacker may steal the user’s device data.
So only ask for the permission that it absolutely needs for the app. Don’t make your app request for access to notification permission if you don’t need them. Keep your permission and access at the bare minimum.
5.Avoid Sensitive information as part of the code.
Don’t include sensitive information in the code like ApiKey use flutter_dotenv package to Load configuration at runtime from a .env file which can be used throughout the application.
6. Block the access of the App when going in the background.
Sometimes we don’t want to enter an app without authorization when going from the background, especially when your app has sensitive data like a credit card number or other financial records.
In flutter, there is WidgetsBindingObserver class. Thanks to this class, we can observe when it is in the background and put your code logic when the app is in paused or inactive state.
In the code logic, you can ask the user to enter a pin/password or ask to unlock the app using biometrics.
7.Update all the dependencies.
Before deploying your app on the store, make sure that all libraries, SDKs, and other dependencies are up to date:
- Keep your Flutter version up to date: You may miss out on important security updates.
- Also, you need to upgrade your package dependencies on time.
8.Protect your application content from view on demand.
When the app goes in the background the task switcher of the device saves a snapshot of the application. If you do not want to show the snapshot of the app you can use secure_application plugin. This plugin allows you to protect your application content from view on demand
9.Check for rooted or jailbroken devices.
This adds an extra layer of security for your application. You shouldn’t run your application on rooted or jailbroken devices. To check if a device is rooted or jailbroken there is a flutter package flutter_jailbreak_detection.
10.Restrict the domain Communication.
You can explicitly whitelist your domain and enable the app to communicate only with allowed domains enforcing HTTPS connection. This requires a native setup for both platform android and iOS side.
1.Network Security Config : Android Side-
i.)Add a network_security_config.xml in app/src/main/res/xml/
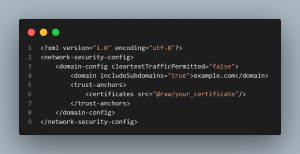
ii.)Now Add-
android:networkSecurityConfig=”@xml/network_security_config” to the <application> tag in app/src/main/AndroidManifest.xml:
<application …>
…
android:resource=”@xml/network_security_config”/>
</application>
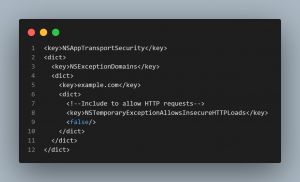
2. NSAppTransportSecurity : iOS Side-
The following snippet should be appended to the Info.plist file under ios/Runner folder
NSExceptionDomains – have all the domains your application needs to communicate






Add comment