In today’s technology-driven world, data security is of utmost importance. As the number of cyber threats increases, ensuring the robustness of web applications becomes a critical aspect of the development process. Security testing is an essential step to identify and fix vulnerabilities before they can be exploited by malicious actors. In this blog, we will explore the process of designing and executing security testing using powerful tools like OWASP ZAP (Zed Attack Proxy) and Burp Suite. These tools are widely used in the industry and offer a comprehensive set of features to evaluate the security posture of web applications. We will dive into practical examples to demonstrate the concepts effectively.
Understanding Security Testing and OWASP ZAP
Security testing involves evaluating an application’s ability to withstand security threats effectively. It encompasses various techniques, including vulnerability assessment, penetration testing, and code review.
OWASP ZAP, an open-source web application security scanner, is one of the most popular tools used for this purpose. It helps developers and security professionals identify potential vulnerabilities and offers the means to address them effectively.
Let’s start by looking at an example of how to use OWASP ZAP to perform a basic security scan on a web application.
Python
# Python script to perform security scan using OWASP ZAP
import time
from zapv2 import ZAPv2
# Configure the ZAP proxy
zap_proxy = ‘http://localhost:8080’
zap = ZAPv2(proxies={‘http’: zap_proxy, ‘https’: zap_proxy})
# Spider the target URL
target_url = ‘http://example.com’
print(f”Spidering target URL: {target_url}”)
zap.spider.scan(target_url)
# Wait for the spider to finish
time.sleep(5)
# Wait for passive scanning to complete
while int(zap.pscan.records_to_scan) > 0:
print(f”Records to passive scan: {zap.pscan.records_to_scan}”)
time.sleep(2)
# Start active scanning
print(“Starting active scan…”)
zap.ascan.scan(target_url)
# Wait for the active scan to finish
while int(zap.ascan.status) < 100:
print(f”Active Scan progress: {zap.ascan.status}%”)
time.sleep(5)
# Generate the report
print(“Generating HTML report…”)
report_html = zap.core.htmlreport()
with open(“zap_report.html”, “w”) as file:
file.write(report_html)
print(“Security scan completed successfully.”)
This Python script sets up the ZAP proxy, spiders the target URL, performs passive scanning, initiates an active scan, and generates an HTML report.
Introduction to Burp Suite and its Capabilities
Burp Suite is another powerful tool used for web application security testing. It offers a plethora of features, making it a preferred choice for both beginners and experienced security professionals. Let’s see how Burp Suite can be used to intercept and manipulate HTTP requests.
Python
# Python script to intercept and manipulate HTTP requests using Burp Suite
import requests
# Configure the Burp Suite proxy
burp_proxy = ‘http://localhost:8080’
proxies = {‘http’: burp_proxy, ‘https’: burp_proxy}
# Send a request to the target URL through Burp Suite
target_url = ‘http://example.com/login’
payload = {‘username’: ‘admin’, ‘password’: ‘pass123’}
response = requests.post(target_url, data=payload, proxies=proxies)
print(response.text)
By setting the burp_proxy in the script, we can intercept and modify HTTP requests made to the target URL through Burp Suite’s proxy. This enables us to understand how the application behaves and identify any potential security flaws.
Identifying Common Vulnerabilities using OWASP ZAP
Now, let’s delve into the practical aspect of security testing using OWASP ZAP. We will explore how to identify common vulnerabilities such as Cross-Site Scripting (XSS) and SQL Injection.
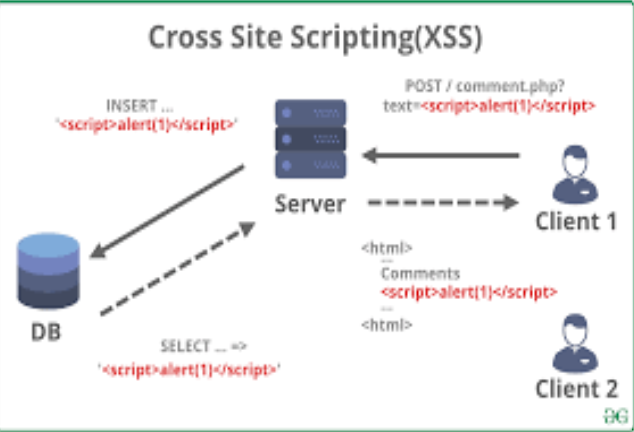
Cross-Site Scripting (XSS) Vulnerability
Cross-Site Scripting (XSS) is a widespread vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. OWASP ZAP can effectively detect and help remediate such vulnerabilities.
Python
# Python script to identify XSS vulnerabilities using OWASP ZAP
import time
from zapv2 import ZAPv2
# Configure the ZAP proxy
zap_proxy = ‘http://localhost:8080’
zap = ZAPv2(proxies={‘http’: zap_proxy, ‘https’: zap_proxy})
# Navigate to the target URL and interact with the application
target_url = ‘http://example.com/contact’
zap.urlopen(target_url)
time.sleep(2)
# Define a payload for XSS attack
payload = ‘<script>alert(“XSS Vulnerability Detected”);</script>’
# Send a POST request with the XSS payload
zap.httpsessions.set_active_session_token(zap.httpsessions.get_list[0][‘token’])
zap.core.set_payload(target_url, payload)
zap.core.send_payloads(target_url, {“”: payload})
# Check the alerts for potential XSS vulnerabilities
alerts = zap.core.alerts()
if any(alert[‘risk’] == ‘High’ and alert[‘alert’] == ‘XSS’ for alert in alerts):
print(“XSS Vulnerability Detected!”)
else:
print(“No XSS Vulnerability Found.”)
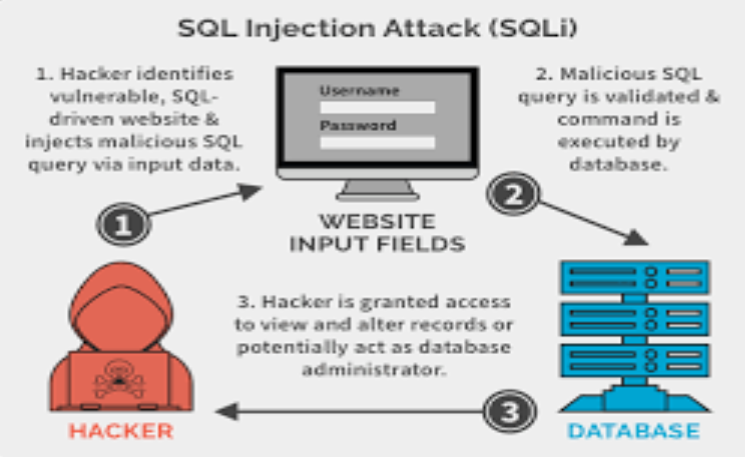
SQL Injection Vulnerability
SQL Injection is a severe vulnerability that allows attackers to manipulate SQL queries in an application’s database, potentially leading to unauthorized data access or deletion. Let’s see how OWASP ZAP can help identify SQL Injection vulnerabilities.
Python
# Python script to identify SQL Injection vulnerabilities using OWASP ZAP
import time
from zapv2 import ZAPv2
# Configure the ZAP proxy
zap_proxy = ‘http://localhost:8080’
zap = ZAPv2(proxies={‘http’: zap_proxy, ‘https’: zap_proxy})
# Navigate to the target URL and interact with the application
target_url = ‘http://example.com/search’
zap.urlopen(target_url)
time.sleep(2)
# Define a payload for SQL Injection attack
payload = “1′ OR ‘1’=’1”
# Send a GET request with the SQL Injection payload
zap.httpsessions.set_active_session_token(zap.httpsessions.get_list[0][‘token’])
zap.core.set_payload(target_url, payload)
zap.core.send_payloads(target_url, {“q”: payload})
# Check the alerts for potential SQL Injection vulnerabilities
alerts = zap.core.alerts()
if any(alert[‘risk’] == ‘High’ and alert[‘alert’] == ‘SQL Injection’ for alert in alerts):
print(“SQL Injection Vulnerability Detected!”)
else:
print(“No SQL Injection Vulnerability Found.”)
Executing Security Testing with Burp Suite
Burp Suite offers comprehensive scanning capabilities that can be leveraged to identify various security vulnerabilities. Let’s see how we can use Burp Suite’s Scanner to perform active scanning and detect potential vulnerabilities.
Python
# Python script to perform active scanning using Burp Suite
from burp import IBurpExtender, IScannerInsertionPointProvider, IScannerInsertionPoint, IScannerCheck, IScanIssue
class BurpExtender(IBurpExtender, IScannerInsertionPointProvider, IScannerCheck):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.setExtensionName(“Burp Security Scan”)
callbacks.registerScannerInsertionPointProvider(self)
callbacks.registerScannerCheck(self)
return
def getInsertionPoints(self, baseRequestResponse):
return [InsertionPoint(baseRequestResponse.getRequest())]
def doPassiveScan(self, baseRequestResponse):
return None
def doActiveScan(self, baseRequestResponse, insertionPoint):
payload = “1′ OR ‘1’=’1”
request = insertionPoint.buildRequest(self._helpers.stringToBytes(payload))
response = self._callbacks.makeHttpRequest(baseRequestResponse.getHttpService(), request)
if b”SQL error” in response.getResponse():
return [CustomScanIssue(
baseRequestResponse.getHttpService(),
self._helpers.analyzeRequest(baseRequestResponse).getUrl(),
[self._callbacks.getScannerInsertionPointName(insertionPoint)],
“SQL Injection”,
“High”,
“The application is vulnerable to SQL Injection.”,
“Fix the SQL Injection vulnerability to prevent potential data breaches.”
)]
return None
class InsertionPoint(IScannerInsertionPoint):
def __init__(self, request):
self._request = request
def getInsertionPointName(self):
return “SQL Injection Point”
def getBaseValue(self):
return self._request
def buildRequest(self, payload):
return self._request[:self.getPayloadOffsets()[0]] + payload + self._request[self.getPayloadOffsets()[1]:]
def getPayloadOffsets(self):
return [self._request.index(b”=”) + 1, len(self._request)]
class CustomScanIssue(IScanIssue):
def __init__(self, httpService, url, insertionPoints, name, severity, detail, background):
self._httpService = httpService
self._url = url
self._insertionPoints = insertionPoints
self._name = name
self._severity = severity
self._detail = detail
self._background = background
def getUrl(self):
return self._url
def getIssueName(self):
return self._name
def getIssueType(self):
return 0
def getSeverity(self):
return self._severity
def getConfidence(self):
return “Certain”
def getIssueBackground(self):
return self._background
def getRemediationBackground(self):
return None
def getIssueDetail(self):
return self._detail
def getRemediationDetail(self):
return None
def getHttpMessages(self):
return None
def getHttpService(self):
return self._httpService
The above script extends Burp Suite’s capabilities by defining a custom Scanner check for SQL Injection. It identifies potential SQL Injection vulnerabilities and provides detailed information about the issue.
Conclusion
In this blog, we explored the significance of security testing and how tools like OWASP ZAP and Burp Suite can be effectively utilized to identify vulnerabilities in web applications. We discussed practical examples to demonstrate the process of designing and executing security testing effectively.
Security testing is a continuous and evolving process that requires vigilance and regular updates. By incorporating robust security testing practices into the development lifecycle, developers and security professionals can ensure that web applications are resilient to potential attacks and safeguard sensitive user data. OWASP ZAP and Burp Suite are just two of the many valuable tools available in the security testing landscape, and leveraging their features can significantly enhance an application’s security posture.
Remember, security is a shared responsibility, and staying proactive in detecting and addressing vulnerabilities is the key to a safer digital landscape. Happy coding and secure testing!





Add comment