In the digital age we are living in, security is paramount. And as they are a key resource, full stack developers play a crucial role in ensuring the safety of web applications.
From the server-side logic to the client-side interfaces, code can be vulnerable to a wide range of security threats. In this blog, we will explore some essential secure coding practices for full-stack developers to help safeguard applications and protect user data.
Input Validation and Sanitization
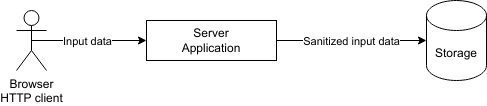
One of the most common security vulnerabilities is insufficient input validation. To prevent attacks like SQL injection and cross-site scripting (XSS), developers will need to always validate and sanitize user inputs. Wondering how?
Here is an example in JavaScript:
javascript
// Bad practice: No input validation
const userInput = req.body.input;
const query = `SELECT * FROM users WHERE username = ‘${userInput}’`;
// Good practice: Input validation and parameterized queries
const userInput = req.body.input;
const sanitizedInput = sanitize(userInput);
const query = `SELECT * FROM users WHERE username = ?`;
db.query(query, [sanitizedInput], (err, results) => {
// Handle results
});
In the above code, we validate and sanitize the user input before using it in an SQL query. This prevents malicious input from compromising the integrity of your database.
Authentication and Authorization

Implementing robust authentication and authorization mechanisms can help you to control access to your application’s resources.
You need to use strong password hashing algorithms and employ multi-factor authentication when necessary.
Let us quickly give you a demonstration through Flask
python
from flask import Flask, request
from flask_bcrypt import Bcrypt
from flask_jwt_extended import JWTManager, create_access_token, jwt_required, get_jwt_identity
# User registration
@app.route(‘/register’, methods=[‘POST’])
def register():
data = request.get_json()
password = bcrypt.generate_password_hash(data[‘password’]).decode(‘utf-8’)
# Store user data securely
# …
# User login
@app.route(‘/login’, methods=[‘POST’])
def login():
data = request.get_json()
# Check credentials and generate an access token
# …
# Protected route
@app.route(‘/protected’, methods=[‘GET’])
@jwt_required()
def protected():
current_user = get_jwt_identity()
# Authorized user access
# …
In this above example, Flask, along with extensions like Flask-Bcrypt and Flask-JWT-Extended, is used to create a secure authentication and authorization system.
Secure API Design
When designing APIs, developers need to consider security from the ground up. You will need to use HTTPS to encrypt data in transit, and implement rate limiting and throttling to prevent abuse.
Also, you can utilize OAuth or API keys for authentication and enforce proper API versioning.
json
// Example API endpoint
GET /api/v1/users
Cross-Site Scripting (XSS) Prevention
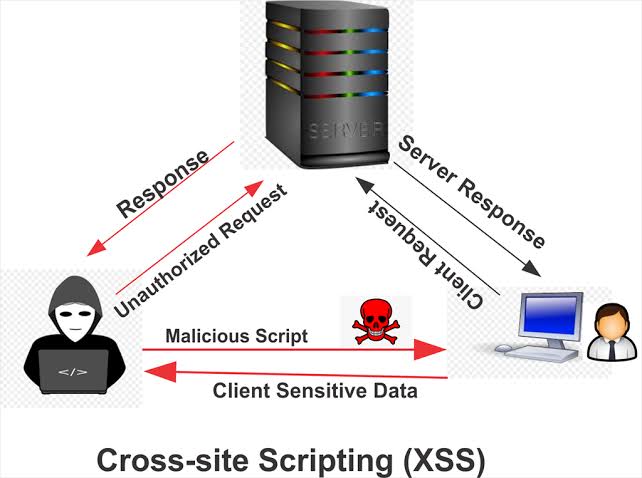
Full stack developers can prevent XSS attacks by escaping user-generated content and avoiding the use of innerHTML to manipulate the DOM.
You will need to use content security policies (CSP) to limit which scripts can be executed on your site.
The below code example will help you understand better.
javascript
// Bad practice: Vulnerable to XSS
const userContent = `<script>alert(‘XSS’);</script>`;
document.getElementById(‘content’).innerHTML = userContent;
// Good practice: Escaping user-generated content
const userContent = `<script>alert(‘XSS’);</script>`;
const textNode = document.createTextNode(userContent);
document.getElementById(‘content’).appendChild(textNode);
Cross-Site Request Forgery (CSRF) Protection
Cross-Site Request Forgery (CSRF) attacks occur when an attacker tricks a user into executing unintended actions on a different website. To protect your application against CSRF attacks:
Generate and Validate Tokens: Generate and validate unique tokens for each request, especially for state-changing actions like POST, PUT, and DELETE.
Here is small example
html
<!– Form with CSRF token –>
<form action=”/update” method=”post”>
<input type=”hidden” name=”csrf_token” value=”{{ csrf_token }}”>
<!– Other form fields –>
</form>
Secure File Uploads
File uploads can be a significant security risk if not handled correctly. Malicious file uploads can lead to various security issues, including the execution of arbitrary code on your server. To secure file uploads, follow these practices:
File Type Validation: You can only allow uploads of specific file types, and validate the file’s content to ensure it matches the expected format.
python
# Python (Flask) example
from werkzeug.utils import secure_filename
def allowed_file(filename):
return ‘.’ in filename and filename.rsplit(‘.’, 1)[1].lower() in {‘png’, ‘jpg’, ‘jpeg’, ‘gif’}
if ‘film’ not in request.files:
return ‘No file part’
file = request.files[‘file’]
if file.filename == ”:
return ‘No selected file’
if file and allowed_file(file.filename):
filename = secure_filename(file.filename)
file.save(os.path.join(app.config[‘UPLOAD_FOLDER’], filename))
File Permissions: Ensure that uploaded files have restricted permissions to prevent execution or access by unauthorized users.
Session Management
Proper session management is essential for maintaining user sessions securely. Thus, developers need to avoid storing sensitive information in client-side cookies, and implement session expiration and regeneration mechanisms.
Here is an example in Node.js using the express-session library
javascript
const express = require(‘express’);
const session = require(‘express-session’);
const app = express();
app.use(session({
secret: ‘supersecretkey’,
resave: false,
saveUninitialized: true,
cookie: { secure: true, maxAge: 60000 } // Configure as needed
}));
In the above example, the session is configured with secure options and a maximum session duration.
Secure Error Handling

Error messages can inadvertently reveal sensitive information about your application. Always handle errors gracefully and avoid exposing stack traces or internal implementation details to users. Instead, log errors internally and provide generic error messages to users:
javascript
// Bad practice: Exposing detailed error messages
app.get(‘/profile’, (req, res) => {
try {
// …
} catch (err) {
res.status(500).send(err.message);
}
});
// Good practice: Providing generic error messages
app.get(‘/profile’, (req, res) => {
try {
// …
} catch (err) {
console.error(err);
res.status(500).send(‘An error occurred. Please try again later.’);
}
});
Conclusion
By following these secure coding practices for full-stack development, you can significantly reduce the risk of security vulnerabilities in your web applications. Security should always be a top priority throughout the development process, from input validation and authentication to secure API design and error handling. In this blog, we have learned that security is important, is an ongoing process, and staying informed about emerging threats and best practices is crucial.
Regularly updating your dependencies, conducting security audits, and engaging in continuous security testing can go a long way to ensuring that your application remains secure.
By integrating these practices into your full-stack development workflow, you will be better equipped to protect your applications and user data from potential security breaches, creating a safer online experience for everyone.






Add comment