Thing to know about EC2 Instance Connect Endpoint —
Previously in any AWS Architecture, the EC2 Instances launched in the Private Subnet had a requirement of Bastion Host/ Jump Server to SSH/RDP (connect).
Now, AWS has launched a Service named EC2 Instance Connect Endpoint to SSH/ RDP to EC2 Instances in Private Subnet Securely without a need of having Bastion Host.
Disadvantages of using Bastion Host?
- Single point of failure: Bastion hosts can become a critical vulnerability as if they fail or get compromised, it can result in a complete loss of remote access.
- Increased complexity: Implementing and managing a bastion host adds intricacy to the network architecture, requiring additional configuration and maintenance
efforts. - Higher costs: Bastion hosts necessitate dedicated resources, leading to increased infrastructure expenses for deployment and upkeep.
- Performance impact: The use of a bastion host can introduce latency and slower connections due to the additional layer of communication between users and private instances.
- Limited scalability: Bastion hosts may face limitations in handling a growing number of concurrent connections, potentially hindering the ability to accommodate expanding infrastructure needs.
HowEC2 Instance Connect Endpoint is Different from EC2 Connect options —
Other EC2 Instance connect options like EC2 Instance Connect, Session Manager, SSH Client, etc. are just an integration to EC2 Service, But EC2 Instance Endpoint Connect is launched as a new service in AWS.
How does it work –
Using IAM based control we can assign specific IAM Users/ SSO Roles permission for Service EC2 Instance Connect Endpoint. So only those users will be able to use that service for connecting to EC2. Network Level access is controlled by the Security Group of EC2 Endpoint Connect.
Advantages of Using EC2 Instance Connect Endpoint
- A) We can connect EC2 Instances in Private Subnet without the need of a Bastion Host/ Jump Server/Public IP.
B) We can now provide access based on IAM identity (User/ Roles) - C) We can Monitor EC2 login activities in CloudTrail, with details of Users, Client IP, Time, Target EC2.
- D) No need for a Client VPN Endpoint or Internet connection just for the sake of SSH/ RDP Connection.
How to Setup EC2 Instance Connect Endpoint
- A) Create an EC2 Instance Endpoint in VPC —
Prerequisite — Create a new Security Group in VPC where you want to create EC2 Instance Endpoint Connect and Open Range of ports (22/1433) from required IP range.
Go to AWS Management Console → Select Service VPC → Select Endpoints → Choose an option to create EC2 Instance Connect Endpoint → Select one of the Private Subnets → Select newly created Security Group → Create. ;
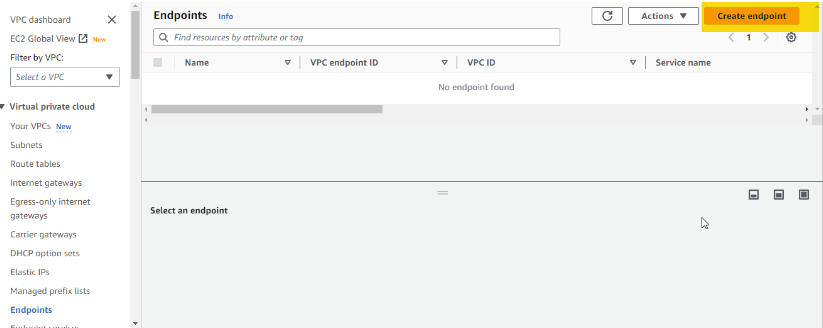
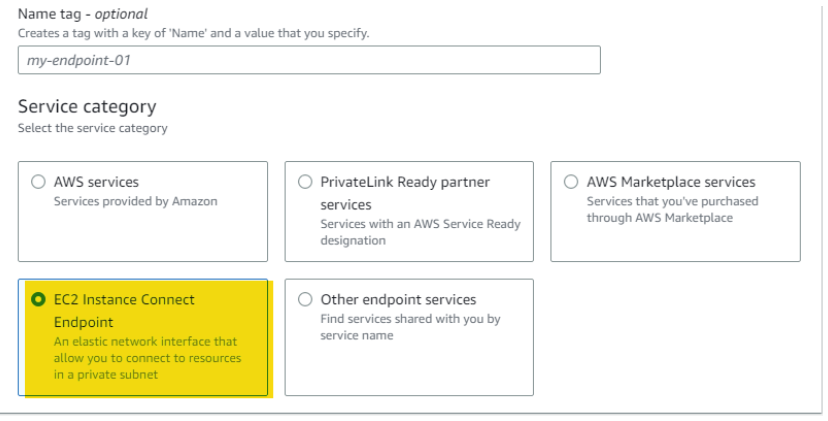
Provide endpoint name and click on EC2 instance Connect endpoint as shown in the snapshot below
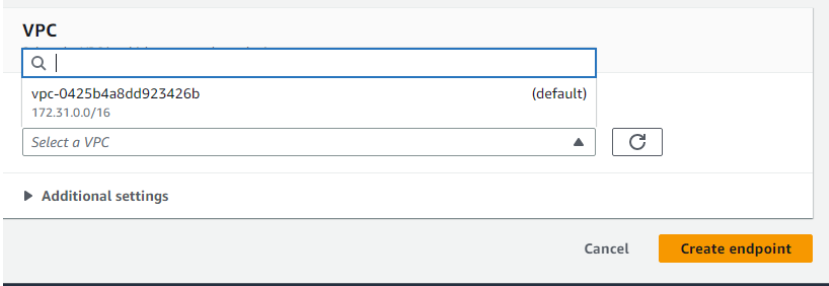
 Select the VPC to which the this endpoint will be connected and click on create endpoint.
Select the VPC to which the this endpoint will be connected and click on create endpoint.
B) Add/Update IAM User/ Role permission for Service EC2 Instance Endpoint Connect. You can refer this JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “VisualEditor0”,
“Effect”: “Allow”,
“Action”: “ec2-instance-connect:*”,
“Resource”: “*”
}
]
}
C) We have to create an IAM User Access Key/Secret Key and configure it in the machine (local) from where you want to do SSH/ RDP.
D) We need to install the latest version of AWS CLI on the machine (local) from where you want to do SSH/ RDP.
Setup is done now, we are good to SSH/ RDP.
Here is the High Level Flow —
i) Level 1 is the AWS IAM Authentication and Authorization. From the local CMD/ terminal when we do SSH/ RDP connection, it actually makes an AWS API call using AWS CLI to the EC2 Endpoint Service with the IAM Access Keys configured.
ii) Level 2 is Network Level Security, Where it check at EC2 Endpoint Service Security Group and then EC2 Instances Security Group to connect to EC2
iii) Level 3 is the Server Level Authentication (For Linux its optional to pass the SSH Key Pair, But for Windows User Password is must)
- How to SSH to Linux EC2 Instances using EC2 Connect Endpoint
For Linux EC2 SSH we have 2 options available to connect using Endpoint Service as using AWS CLI and SSH with Proxy.
A) Using AWS CLI
Make sure the machine has AWS CLI latest version and Access Key configured with permission of ‘ec2-instance-connect’. Then fire below command to connect to the AWS EC2 Linux Instance by replacing the instance-id.
aws ec2-instance-connect ssh –instance-id i-0123456789
B) Using SSH with Proxy
For this you need OpenSSH and AWS CLI with proper access to be configured. Use the below command and replace the instance-id and Keypair location
ssh ec2-user@i-0123456789 -i C:\LocationToKeypair.pem -o ProxyCommand=”aws ec2-instance-connect open-tunnel –instance-id %h”
C) Using AWS Console —
For Linux EC2 instances we can use the AWS EC2 Console — Connect option — with EC2 Instance Connect — Using EC2 Connect Endpoint, which allows connection to Private IP using the selected endpoint as shown below
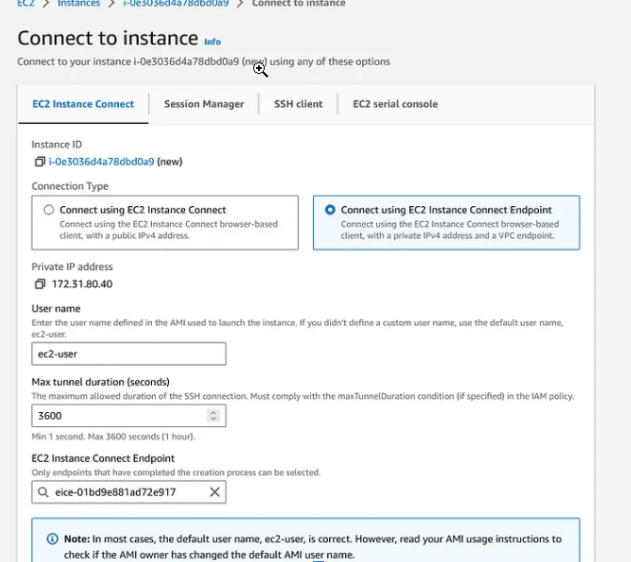
- How to RDP to Windows EC2 Instances using EC2 Connect Endpoint
To connect to Windows EC2/ to RDP, we need to create a tunnel on the local machine/ device from which we need to make RDP connection to EC2. We can use any local available port for tunnel
Use this command to create Tunnel from CMD (replace instance-id and local port)
aws ec2-instance-connect open-tunnel –instance-id i-0f123456755 –remote-port 3389 –local-port 9090
Now a tunnel will be created and you can see the message on CMD.
Now use any RDP application and use these config —
IP — localhost:9090 (Port is the Local Port)
Username — Administrator OR AD Username
Password — Windows Password retrieved from Console OR AD Credentials.
With this now you have got enough idea on the EC2 Instance Endpoint Connect and how easy it’s to use.
EC2 Instance Connect Endpoint is free to use but we get standard data transfer charges in AWS.






Add comment