Introduction
Whether we are aware or not, the network infrastructure, servers, and applications we have in our staging and production environments may have vulnerabilities that attackers can take advantage of. For example, let’s say that we are using a misconfigured Redis server in our staging environment and we mistakenly left the port open for anything outside of the VPC to access it. Depending on how fast this server gets compromised (minutes to hours), we may find this cache server doing something else — attacking other servers. At this point, the best assumption to make is that this server can no longer be trusted and other systems connected to it might have been compromised as well. This is something we all wish to avoid and this is one of the reasons why we should audit and ensure the overall security of our systems. One of the ways to prevent these issues from happening is to use vulnerability scanning tools which look for relevant vulnerabilities in our systems.
If we already have container images in ECR along with running EC2 instances in our AWS account, one of the more convenient ways to incorporate automated security assessments is through the use of Amazon Inspector. In addition to the other major upgrades, the new version of Amazon Inspector has replaced the periodic and manual scanning approach with continual automated scans. The cool thing here is that Amazon Inspector automatically detects the EC2 instances and container images in our account and then performs the assessment scan when a “change” is performed. Of course, all newly detected instances and container images get scanned as well upon detection. This new way of using Amazon Inspector makes things much more scalable and practical long term.
Detecting and Scanning Container Images for Vulnerabilities
To test Amazon Inspector’s capability to detect and automatically scan container images, we simply create a new ECR repository and push a sample vulnerable container image such as a container image that contains DVWA (D*** Vulnerable Web Application)
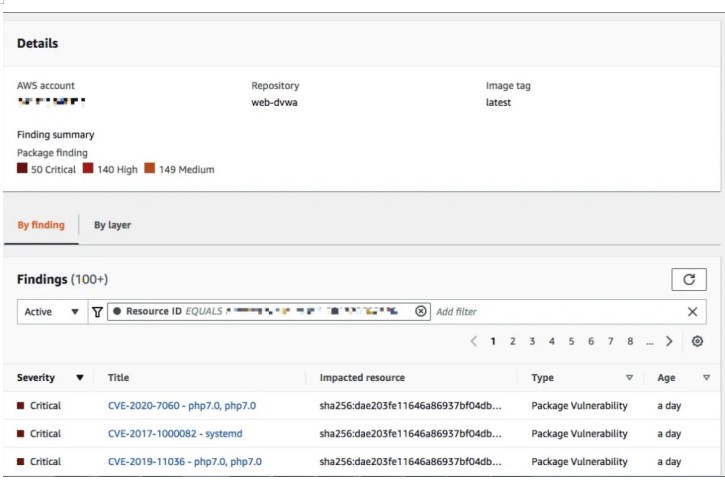
After a few minutes, we are able to see that there are 50 Critical issues found by Amazon Inspector.
By clicking the title link, we are able to see a few more details regarding one of the reported issues.
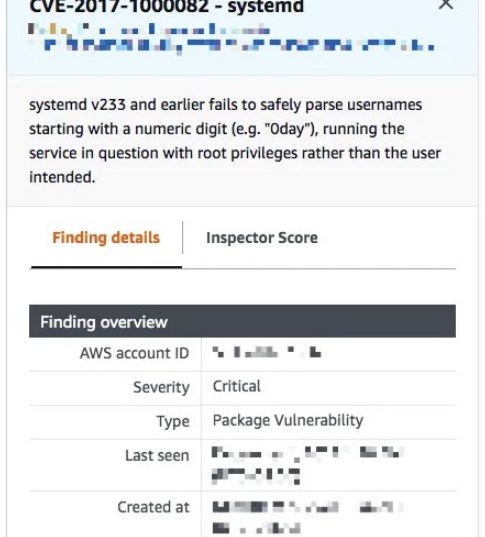
If we scroll down a bit, we should be able to see a link that opens a reference with more information about this vulnerability.
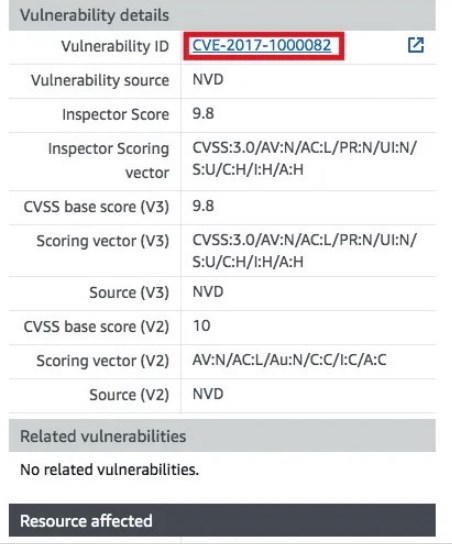
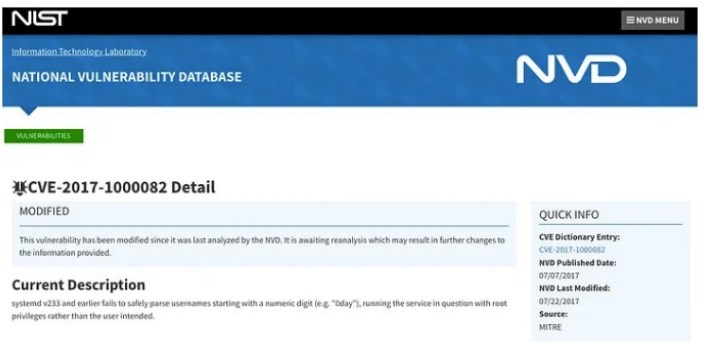
Clicking the Vulnerability ID link, the following page should open:
Detecting and Scanning EC2 Instances for Vulnerabilities
To test Amazon Inspector’s capability to detect and automatically scan EC2 instances, we simply launch any instance in an existing VPC. For this example, we launched a new Cloud9 instance using the Amazon Linux 2 image. After a few minutes after instance launch, the new instance should be seen in the Account management page (and in other relevant pages as well) inside the Amazon Inspector console.
If the target instance can not be detected by Amazon Inspector (e.g., Status = “Unmanaged EC2 instance”), click “Unmanaged EC2 instance” and then click “these instructions”
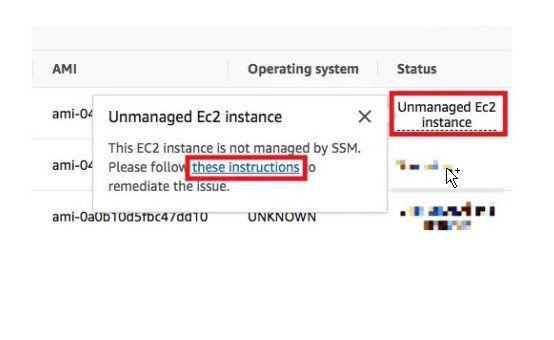
This should open the Execute automation document page within Systems Manager which we will use to troubleshoot what’s wrong with the setup and configuration.
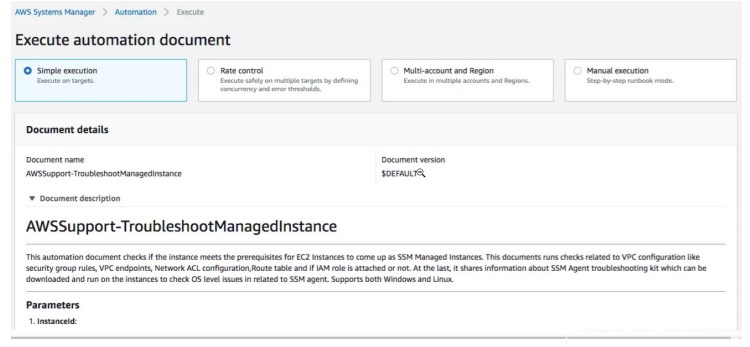
We simply input the instance ID and then click “Execute”. After a few minutes, the executed automation should give us the debugging information we need to fix the setup.

The first thing we need to ensure is that the IAM role used by the instance has the AmazonSSMManagedInstanceCore policy attached.
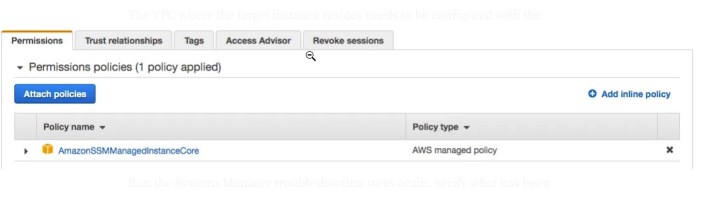
We do this by creating a new IAM role (or using an existing one) and attaching the AmazonSSMManagedInstanceCore policy.
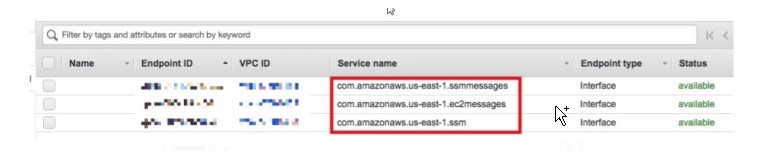
The VPC where the target instance resides needs to be configured with the relevant VPC endpoints as well.
Run the Systems Manager troubleshooting steps again, verify what has been fixed already, and then fix the rest of the reported configuration issues. Once everything has been configured properly, then we should see Amazon Inspector scanning the instance.
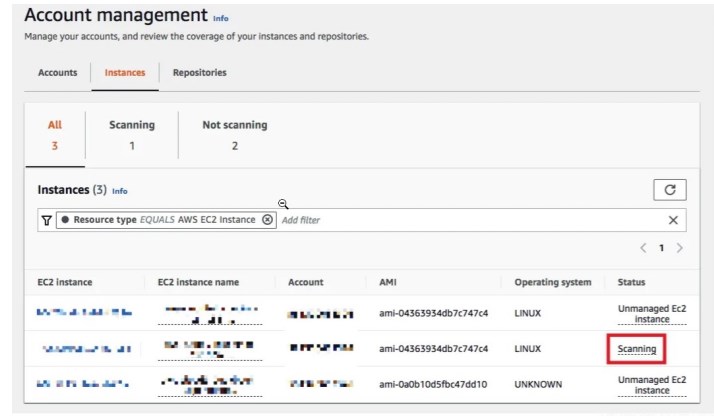 few After a few minutes, we should see the reported vulnerabilities by the scan.
few After a few minutes, we should see the reported vulnerabilities by the scan.
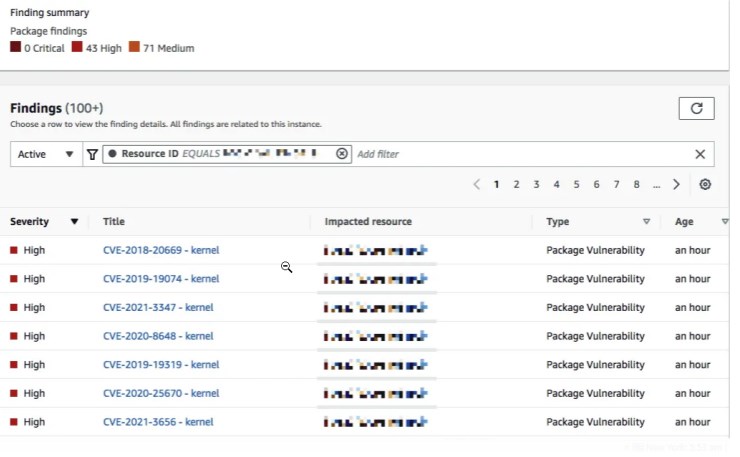
Following the same set of steps as with Part II where we scanned a vulnerable container image, we should see a page similar to what is shown in the image below.
Why should you use Amazon Inspector?
As we can see, getting Amazon Inspector to work in our accounts is simple and straightforward. It might take a few minutes to set it up to get it to work with EC2 instances but this effort is easily rewarded with the continuous assessment and scan of the resources involved. If something changes in the EC2 instance, Amazon Inspector will detect things and run the additional scans automatically without us having to trigger these scans manually (similar to how it is done in Amazon Inspector Classic).
Advantages:
Automatic Scanner:
Amazon Inspector automatically detects security vulnerabilities and compliance issues. This automates the processes that would otherwise require manual effort, allowing you to obtain faster results.
Compliance Controls:
Businesses may have to meet specific compliance requirements. Amazon Inspector provides compliance controls that ensure AWS services and workloads meet these requirements.
Comprehensive Reporting:
Amazon Inspector offers detailed reports based on the scanner results. These reports help you understand the detected security vulnerabilities and compliance issues and provide recommendations to address them.
Easy Integration:
Amazon Inspector can easily integrate with your existing AWS infrastructure. This ensures compatibility with your current AWS environment and allows you to launch the scanner quickly.
Disadvantages:
Customization Challenges:
Amazon Inspector may have limitations in terms of customization options. This may require some users to rely on additional tools or methods to meet specific requirements.
Processing Time:
Amazon Inspector may require extensive scans, resulting in longer processing times. This can potentially lead to performance issues in large-scale applications or infrastructures.
Additional Cost:
When using Amazon Inspector, it is important to consider the cost of the service. The cost of using the service can vary depending on the scanning frequency, the number of resources scanned, and reporting needs.
Amazon Inspector is an effective service that helps you scan your AWS infrastructure and applications to detect security vulnerabilities and compliance issues. It offers advantages such as automatic scanning, compliance controls, comprehensive reporting, and easy integration.
However, it would help if you also considered its disadvantages, including customization challenges, processing time, and potential additional costs.
In addition to Amazon Inspector, it’s important to consider other alternative services.
Popular alternatives to Amazon Inspector:
Nessus:
Nessus is a vulnerability scanner offered by Tenable. It is used to detect security vulnerabilities in systems and applications across networks. Nessus has a comprehensive vulnerability database and can scan many common vulnerabilities. It also provides customization options and extensive integration capabilities.
Qualys:
Qualys is a cloud-based security and compliance service. It is used to detect security vulnerabilities and compliance issues in network and application layers. Qualys offers a comprehensive scanner and can perform compliance checks for various industry standards (such as PCI DSS, HIPAA, etc.). It also provides effective reporting features and wide integration options.
OpenVAS:
OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanner. It is used to detect security vulnerabilities in systems and applications across networks. OpenVAS has a wide vulnerability database and can be customized to meet user requirements. It also provides reporting and integration capabilities.
Rapid7 InsightVM:
Rapid7 InsightVM is a service for network security and risk management. It is used to detect security vulnerabilities, analyze risks, and perform compliance checks on systems. Rapid7 InsightVM offers a comprehensive scanner and rich reporting features. It also provides effective workflow features to help users prioritize and manage the remediation process.
Conclusion:
These alternative services have their own advantages and disadvantages compared to Amazon Inspector. Some services may have broader features and customization options, while others may be more cost effective or easier to integrate. To determine which service is best for you, it’s important to consider your requirements, budget, and priorities.






Add comment