In the intricate landscape of networking and connectivity management within a multi-account AWS environment, precision and efficiency are paramount.
In this article, we will provide you with a detailed breakdown of the specific networking solutions
Enhancing VPC Performance: Guaranteeing Workload Availability, Security, and Scalability
Within our cloud ecosystem, the AWS Virtual Private Cloud (VPC) plays a pivotal role. It not only forms the bedrock for workload deployment but also acts as a critical security barrier. Our solution elevates VPC functionality by segmenting it into multiple subnets across various availability zones, thereby reinforcing security and availability measures. Additionally, through the efficient utilization of AWS VPC IP Address Manager (AWS IPAM), we ensure the scalability of the VPC infrastructure by meticulously assigning IP addresses. This alignment is with our specific requirements ensures seamless growth and operational excellence.
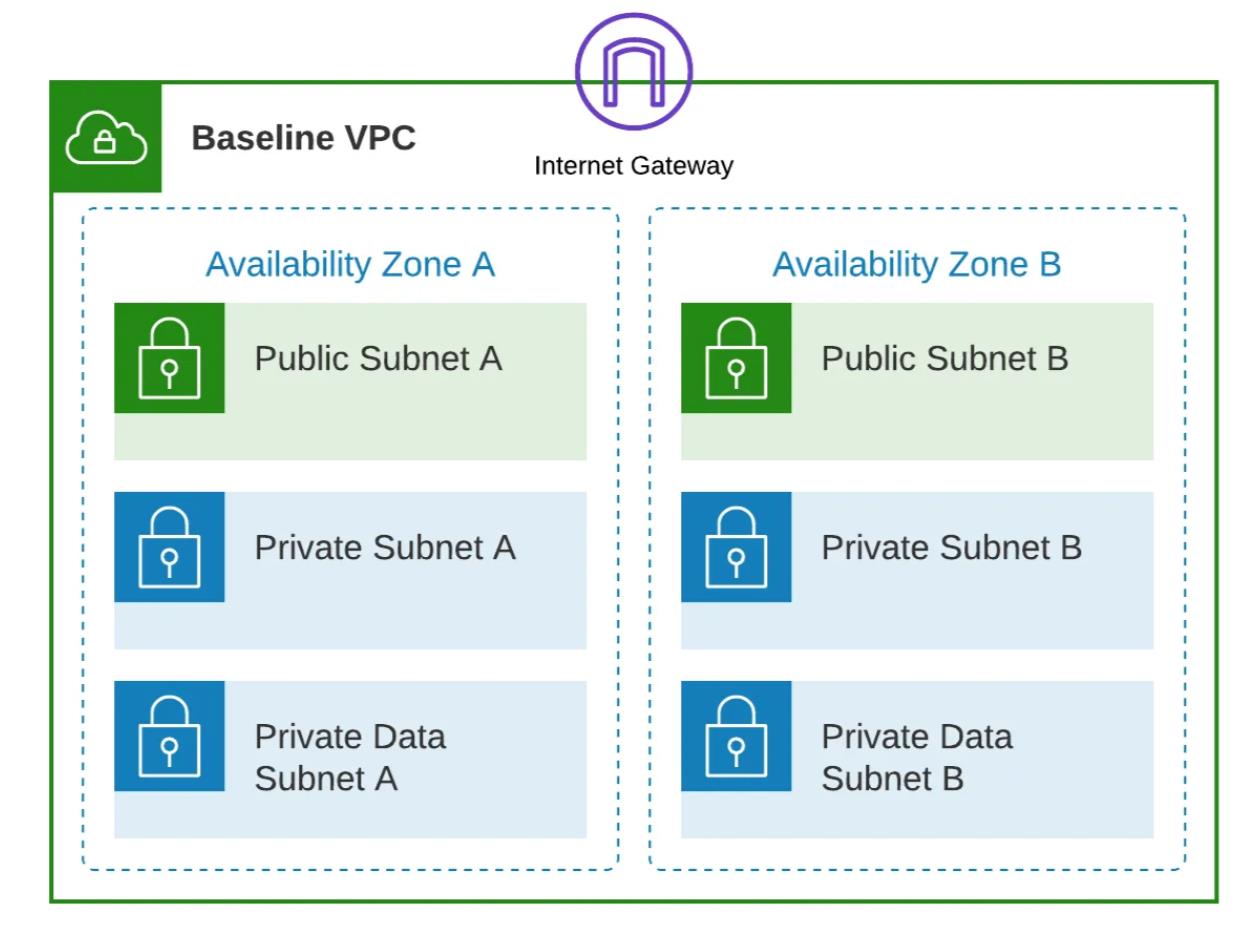
The above diagram depicts the foundational VPC structure tailored to host workloads within our entire organization. This standardized VPC configuration is designed to deliver a uniform and secure environment for workloads, ensuring consistency and robust security measures organization-wide.
Strengthening Security Through Subnet Segmentation
In our pursuit of bolstering VPC security, our solution introduces three distinct types of subnets: public, private, and private data subnets. These subnets have been meticulously crafted to optimize both security and resource allocation.
The ‘public’ subnet, as the name suggests, caters to resources that require public accessibility. It’s ideally suited for public-facing elements like load balancers. In line with best practices, we reserved the ‘private’ subnet for workloads and applications. This subnet is isolated from direct external access, fortifying security for internal resources. In contrast, the ‘private data’ subnet is exclusively earmarked for data storage and databases. It provides a segregated environment for sensitive data, adding additional layers of security.
This strategy of subnet segmentation not only enhances security but also streamlines resource allocation within the VPC. It aligns perfectly with our customer’s need for a well-structured and secure cloud environment.
Optimizing Availability: Harnessing the Power of Multiple Availability Zones
In our proposed design, we strategically position each subnet, including public, private, and private data subnets, across multiple availability zones. These availability zones are engineered to remain isolated from each other, effectively minimizing the impact of any potential failures. By distributing subnets across availability zones, we significantly enhance fault tolerance and network resilience. This approach guarantees high availability and reliability for our customer’s critical workloads.
Precision Scaling: CIDR Allocation and AWS IPAM Integration
Scalability is a vital consideration in any business, especially within the dynamic realm of cloud environments. To support seamless growth, each VPC seamlessly integrates with AWS VPC IP Address Manager (AWS IPAM). This integration ensures the allocation of CIDRs is purposefully designed for scalability. By adopting this approach, workloads can effortlessly scale, enhancing overall resilience and operational efficiency. This means that as the business expands, the infrastructure can adapt swiftly to meet evolving demands.
Centralized Networking for Security and Efficiency
With a focus on security, scalability, and operational efficiency, our comprehensive analysis leads us to recommend the adoption of a centralized transitive routing approach. This approach is the ideal solution for managing our customer’s network connectivity effectively. It involves establishing a dedicated networking account, serving as the central hub for networking constructs, resources, routing paths, and protocols across all AWS accounts and on-premises locations. This centralized approach empowers our customer’s central networking team to efficiently manage network operations.
Harnessing the Power of Transit Gateway (TGW)
At the core of our networking architecture lies the strategic deployment of a Transit Gateway (TGW) within the dedicated networking account. This deliberate choice empowers us to effortlessly connect VPCs from various accounts within our AWS organization to the TGW. The TGW takes on the responsibility of managing custom route tables and connectivity permissions, simplifying the configuration process for all networking and connectivity requirements.
Seamless VPC Interactions through Transit Gateway Attachments
Transit Gateway plays a pivotal role in simplifying and facilitating communication between VPCs, all without the need for intricate peering configurations, especially when dealing with scale. This is achieved by configuring transit gateway attachments for each VPC. Once these VPCs are set up and attached to the transit gateway, the flow of packets to and from these VPCs becomes a straightforward and manageable process.
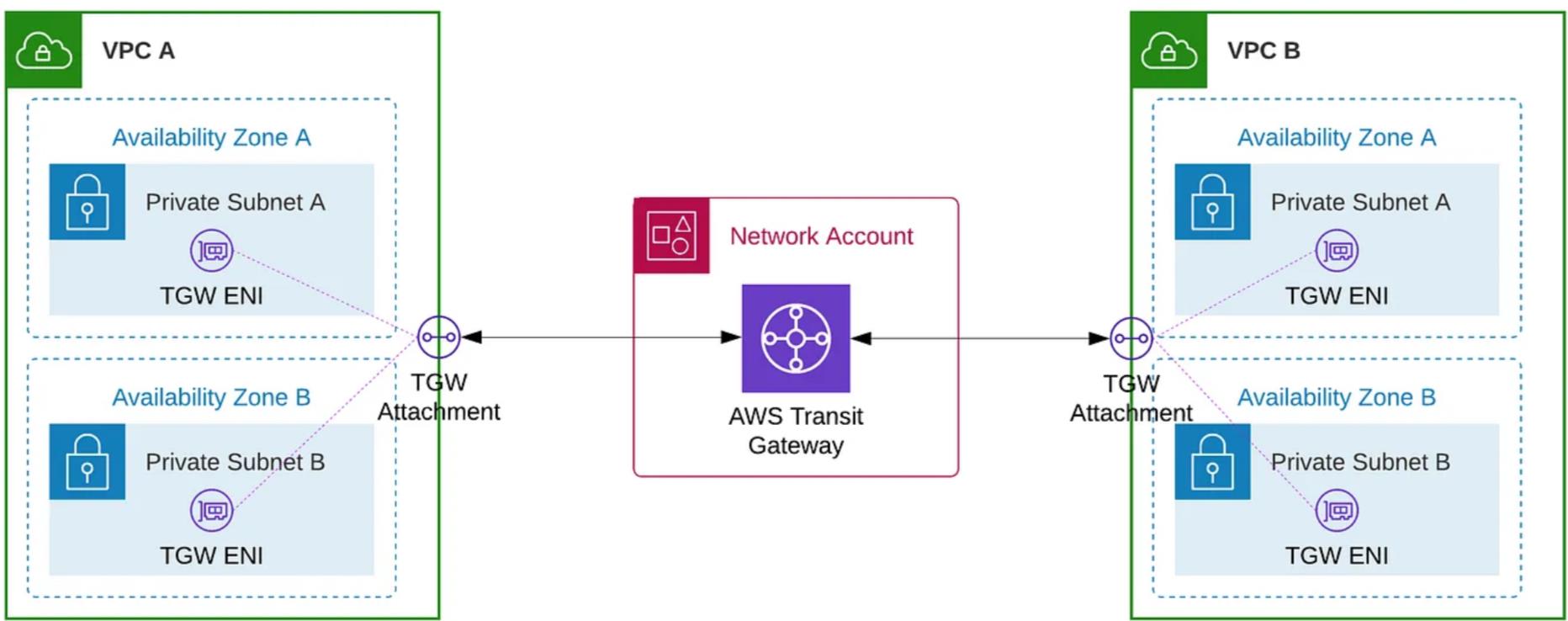
As shown in the above diagram, our design incorporates the use of Elastic Network Interfaces (ENIs) across multiple Availability Zones to facilitate the routing of traffic to the VPCs. This architectural choice guarantees highly available connections to the transit gateway, thereby promoting robust and efficient communication between VPCs within our AWS environment.
Moreover, for optimal management of traffic within the workload VPCs, the VPC route tables for the private and private data subnets are meticulously configured to include a default route directed toward the transit gateway. This specific setup ensures that all outbound traffic from these subnets is efficiently directed through the transit gateway as the next hop.
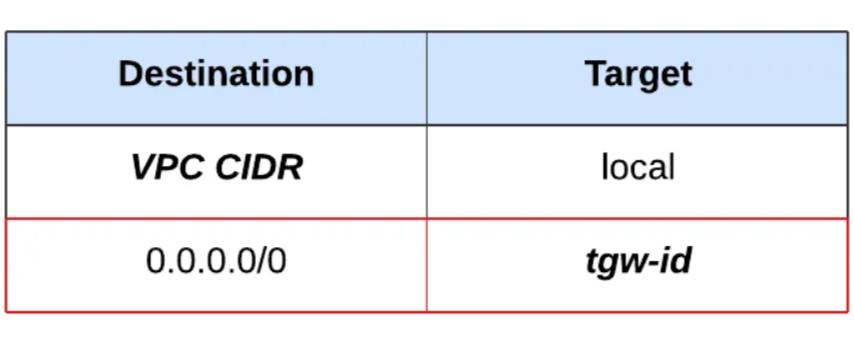
The above table illustrates the standard private route table configuration, meticulously crafted to meet the routing requirements of the workload VPCs. This routing strategy not only streamlines network management but also optimizes traffic routing within the AWS environment, enhancing overall efficiency.
Effective Security and Traffic Management: Utilizing TGW Route Tables for Environment Segmentation
In the realm of cloud computing, the security of the production environment holds utmost significance. A key component of this security strategy is maintaining a distinct segmentation between production and non-production traffic. Our design takes a rigorous approach to separate and segment various environments, safeguarding the integrity and security of each in a meticulously planned manner.
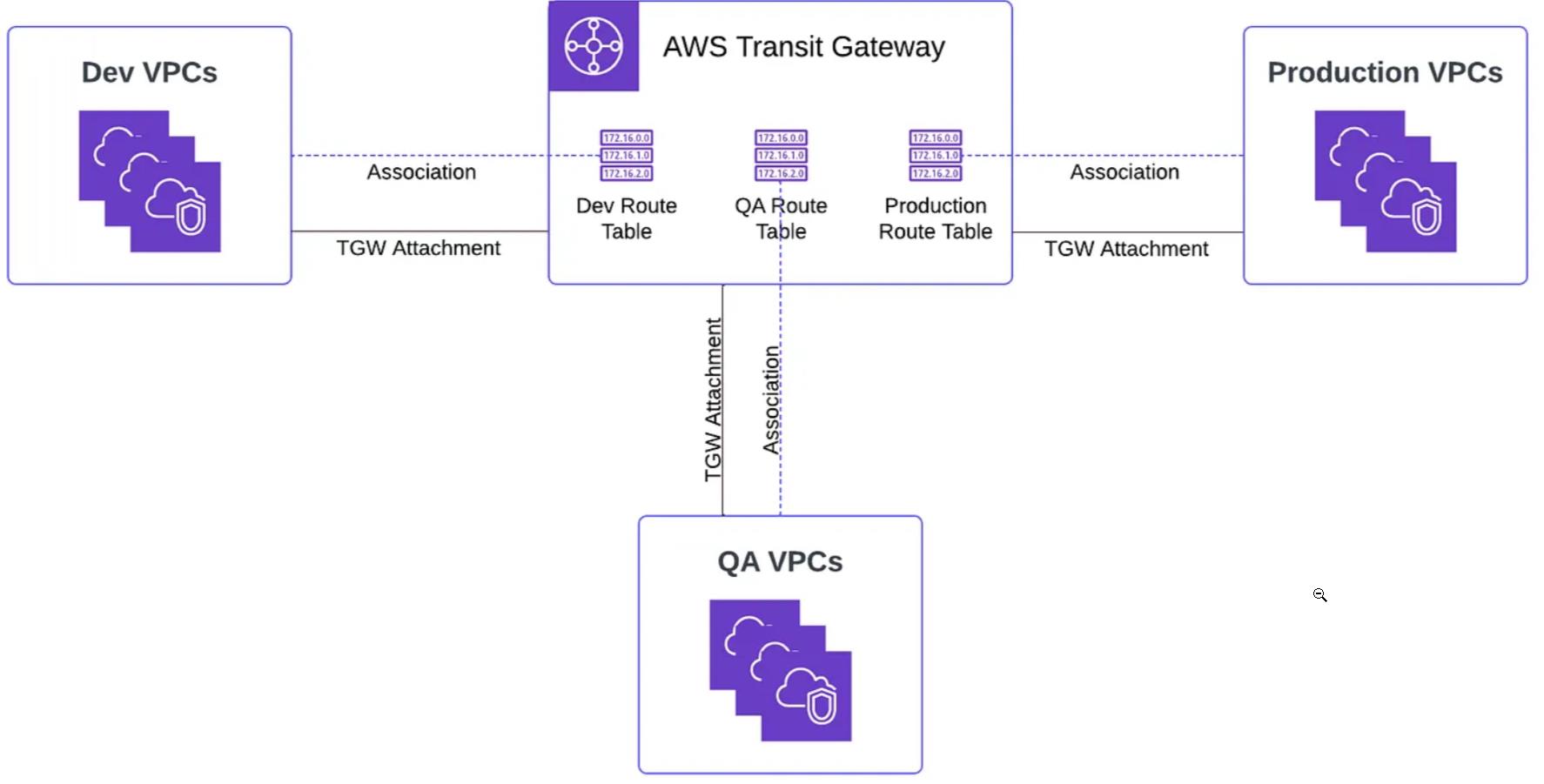 In pursuit of this objective, we harness the capabilities of TGW route tables, empowering us to efficiently control and segment traffic flows. As depicted in the above diagram, this design provides a visual representation of how traffic is systematically segmented using these route tables. We enforce stringent security measures by aligning each environment with its designated route table. For instance, production VPCs exclusively connect to the production transit gateway route table, ensuring the precise segmentation of traffic and the configuration of authorized communications between specific environments.
In pursuit of this objective, we harness the capabilities of TGW route tables, empowering us to efficiently control and segment traffic flows. As depicted in the above diagram, this design provides a visual representation of how traffic is systematically segmented using these route tables. We enforce stringent security measures by aligning each environment with its designated route table. For instance, production VPCs exclusively connect to the production transit gateway route table, ensuring the precise segmentation of traffic and the configuration of authorized communications between specific environments.
Enhancing Outbound Connectivity: Embracing a Centralized Egress Approach
Through our extensive collaboration with our client during the assessment phase, it became evident that migrated workloads would necessitate outbound internet connectivity. However, our robust security configuration inherently isolates workloads in private subnets from external access as a default measure. To effectively address this requirement, our proposal introduces the deployment of a centralized egress VPC within the dedicated networking account. The upcoming sections will provide in-depth insights into how this solution aligns with and harnesses the concepts discussed earlier.
Cost-Effective Scaling with Centralized NAT Gateways
In our centralized design, all internet-bound traffic is channeled through the centralized egress VPC. This consolidation of outbound connectivity within a dedicated VPC empowers our customer to efficiently manage and optimize the resources required for internet access across the entire organization. This centralized approach offers precise cost control, minimizing expenses associated with deploying individual resources for outbound connectivity in each VPC.
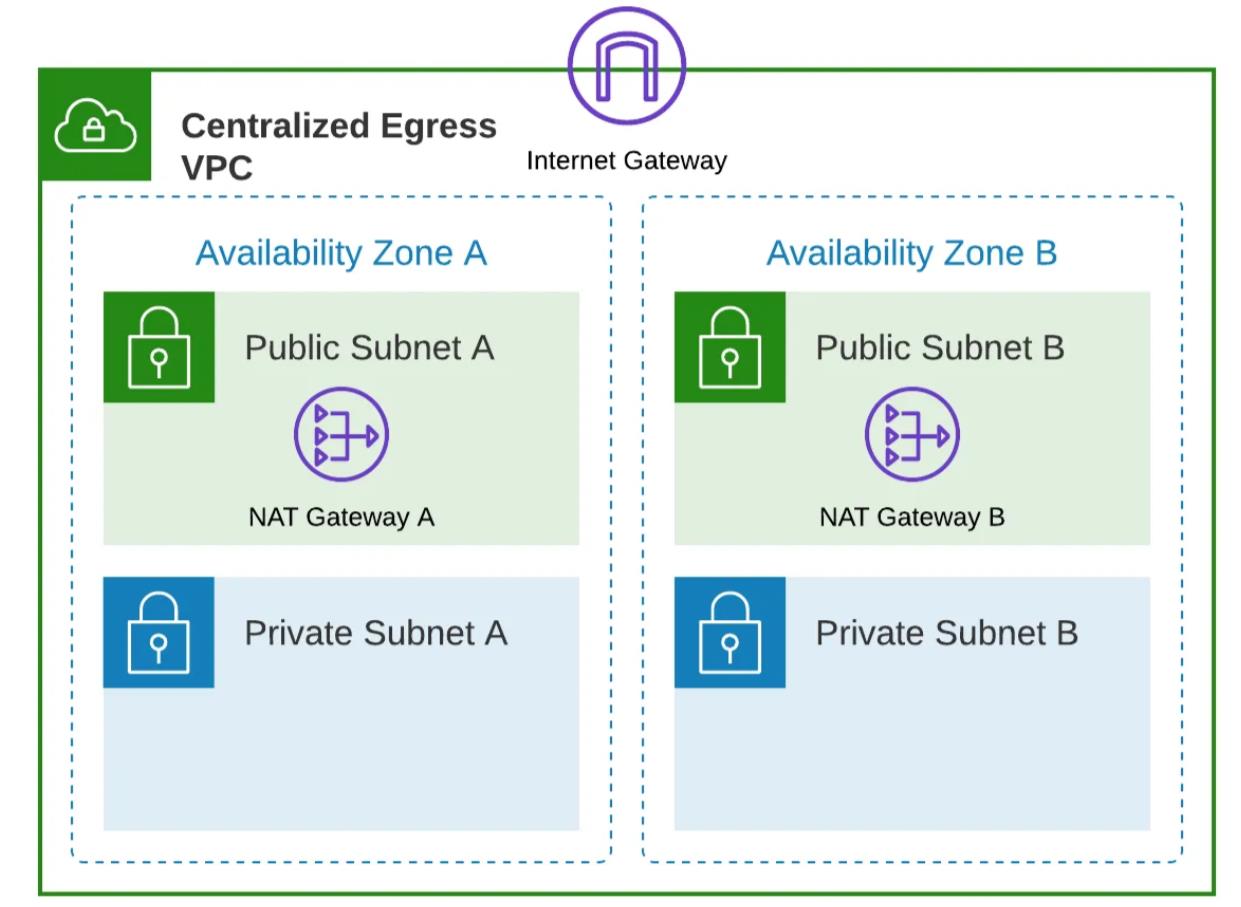
The above diagram offers a visual insight into the structured framework of the centralized egress VPC within our design. This VPC has been meticulously organized to serve distinct purposes, aligning seamlessly with our requirements for outbound internet connectivity.
The VPC is composed of both public and private subnets. The public subnet is specifically reserved to host the Network Address Translation (NAT) gateway, a critical component for outbound connectivity. In contrast, the private subnet is strategically designed to accommodate potential future implementations of security devices for monitoring outbound traffic.
Furthermore, akin to the workload baseline VPC, the subnets within the centralized egress VPC have been configured to span multiple availability zones. This multi-Availability Zone architecture ensures a high level of availability and redundancy for the VPC’s resources, thereby guaranteeing uninterrupted internet access.
Enhancing Security through Centralized Egress Traffic Monitoring with VPC Flow Logs
Centralizing outbound traffic not only presents cost-efficiency benefits but also bolsters security by establishing a central hub for monitoring all outgoing traffic. This centralized observation and control point serves as an effective means of monitoring and securing internet-bound traffic, aligning seamlessly with our stringent security requirements.
One effective approach to realize this strategy is by enabling VPC Flow Logs within the centralized outbound VPC. These logs comprehensively capture all IP traffic to and from the VPC, offering a robust record of outbound activities. This logging capability enables visibility, analysis, and alerting for outbound traffic, significantly enhancing security monitoring and compliance endeavors.
By integrating VPC Flow Logs into the design of the centralized egress VPC, we can proactively detect and respond to security events, ensuring a robust security posture for outbound internet connectivity within their AWS environment.
Implementing a Centralized Outbound Approach via Shared TGW Route Tables
The implementation of a centralized outbound connectivity approach leverages the transit gateway’s transitive routing capabilities effectively. By strategically utilizing transit gateway attachments and route tables, traffic from the workload VPCs can be seamlessly configured to align with this centralized approach.
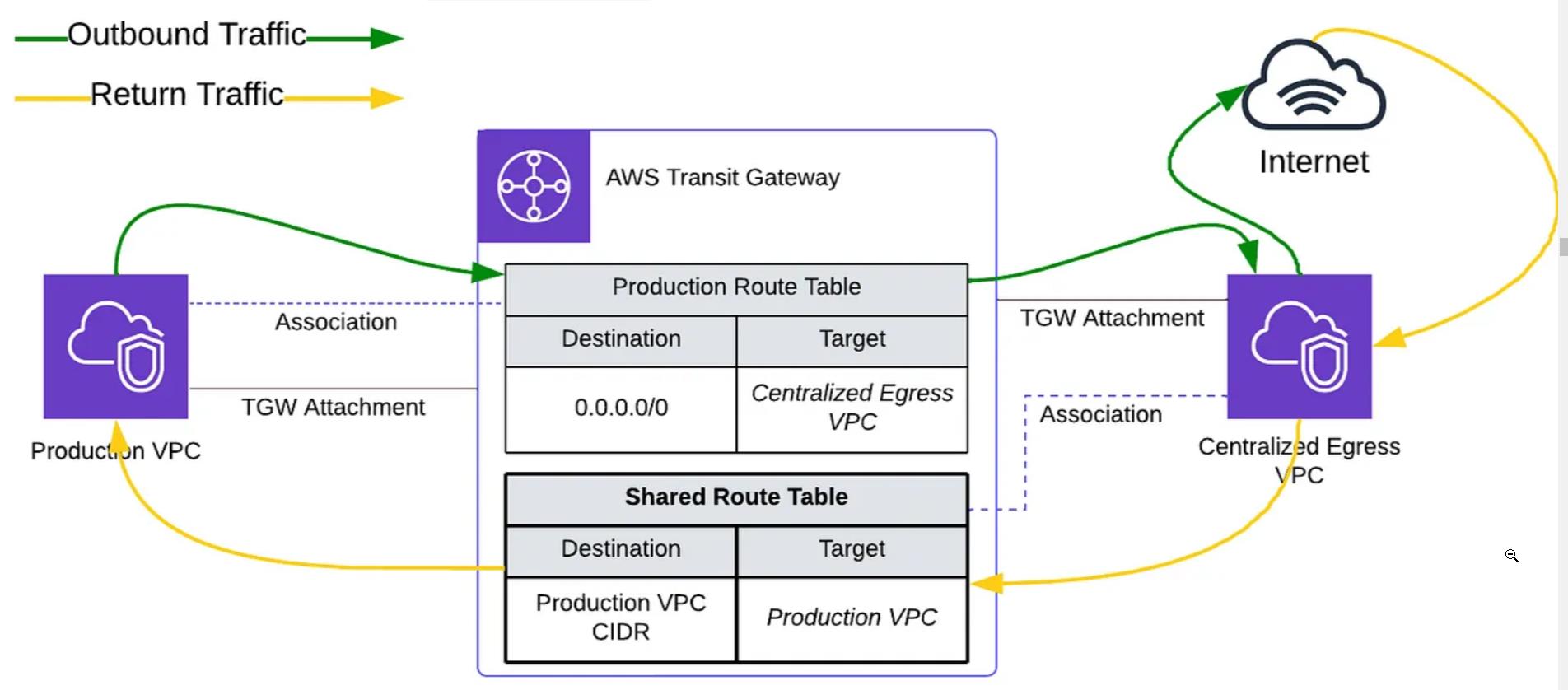
The above diagram provides a visual representation of the traffic flow for outbound connectivity from a Production VPC to the centralized egress VPC and back, facilitated by the configured route tables. The associations with these route tables play a pivotal role in directing traffic efficiently. Here’s a detailed breakdown of how this traffic flow is achieved:
- Initiating Outbound Traffic: Workload VPCs, such as the Production VPC, direct their outbound traffic to the centralized egress VPC. They achieve this by utilizing specific route tables associated with their respective attachments. Within these route tables, a static route is defined to ensure that traffic is directed towards the centralized egress VPC for outbound connectivity.
- Centralized Egress VPC: This VPC, with its public subnet housing the NAT gateway, acts as the gateway for outbound internet-bound traffic. It effectively directs this traffic to its intended destination on the internet.
- Managing Return Traffic: To complete the traffic flow loop, return traffic from the internet is directed back to the centralized egress VPC. To ensure that this return traffic reaches the appropriate workload VPC (Production), the centralized egress VPC is associated with a shared route table containing the propagated CIDR of the Production VPC. This association ensures the return traffic is correctly routed to its destination, thereby completing the bidirectional flow.
Centralizing Inbound Traffic Management: The Power of a Centralized Ingress Approach
In alignment with our centralization strategy, our proposal extends to the centralization of inbound traffic by configuring a dedicated centralized ingress VPC. This specialized VPC acts as the central entry point for all of our customer’s public-facing resources, bringing forth several noteworthy advantages. The following sections will delve into the intricacies of this strategy.
Efficient Inbound Traffic Management with Application Load Balancers
The centralized ingress VPC serves as a hub for streamlined inbound traffic management. It consolidates and regulates the flow of incoming requests to public-facing resources, greatly enhancing the efficiency of external access management. Furthermore, by directing incoming traffic through this dedicated ingress VPC, we can implement robust security measures at a single point of control. This centralized approach not only fortifies security but also simplifies the management of security policies across multiple VPCs.
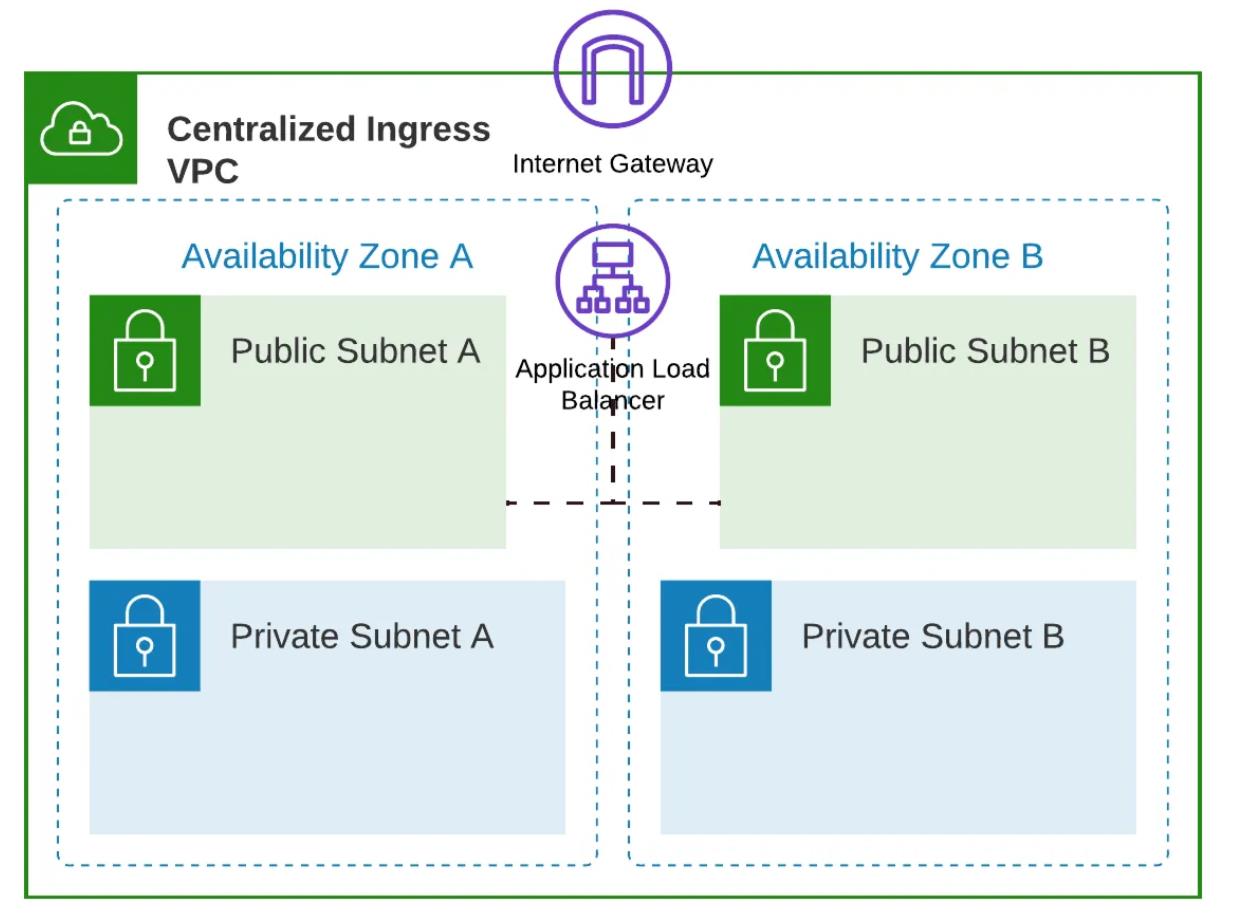
Similar to the egress VPC, centralized ingress VPC, as shown in the above diagram, is composed of both public and private subnets. The public subnet is explicitly reserved to host the Application Load Balancer (ALB), a pivotal component for serving incoming requests. On the other hand, the private subnet is designed to accommodate potential future implementations of security devices for monitoring inbound traffic.
Furthermore, akin to the workload baseline VPC, the subnets within the centralized ingress VPC have been meticulously configured to span multiple availability zones. This multi-Availability Zone architecture empowers the Application Load Balancer with cross-zone load balancing capabilities, ensuring a high level of availability and redundancy for our customer’s critical workloads.
Enhancing Security with Centralized Ingress Traffic Monitoring Using VPC Flow Logs
Centralizing inbound traffic not only improves security but also establishes a central hub for monitoring all incoming traffic. This single point of observation and control provides an effective means of monitoring and securing public-facing workloads, perfectly aligning with our stringent security requirements.
To achieve this strategy, we once again employ VPC Flow Logs within the centralized ingress VPC. These logs capture a comprehensive record of all IP traffic to and from the VPC, effectively documenting ingress activities for the organization. This logging capability offers visibility, analysis, and alerting for inbound traffic, significantly enhancing security monitoring and compliance efforts.
Implementing a Centralized Ingress Approach through a Shared TGW Route Table
The implementation of a centralized inbound connectivity approach is facilitated by the transit gateway’s transitive routing capabilities. By strategically harnessing transit gateway attachments and route tables, internet traffic directed towards the public-facing workload VPCs can be seamlessly configured to align with this centralized approach.
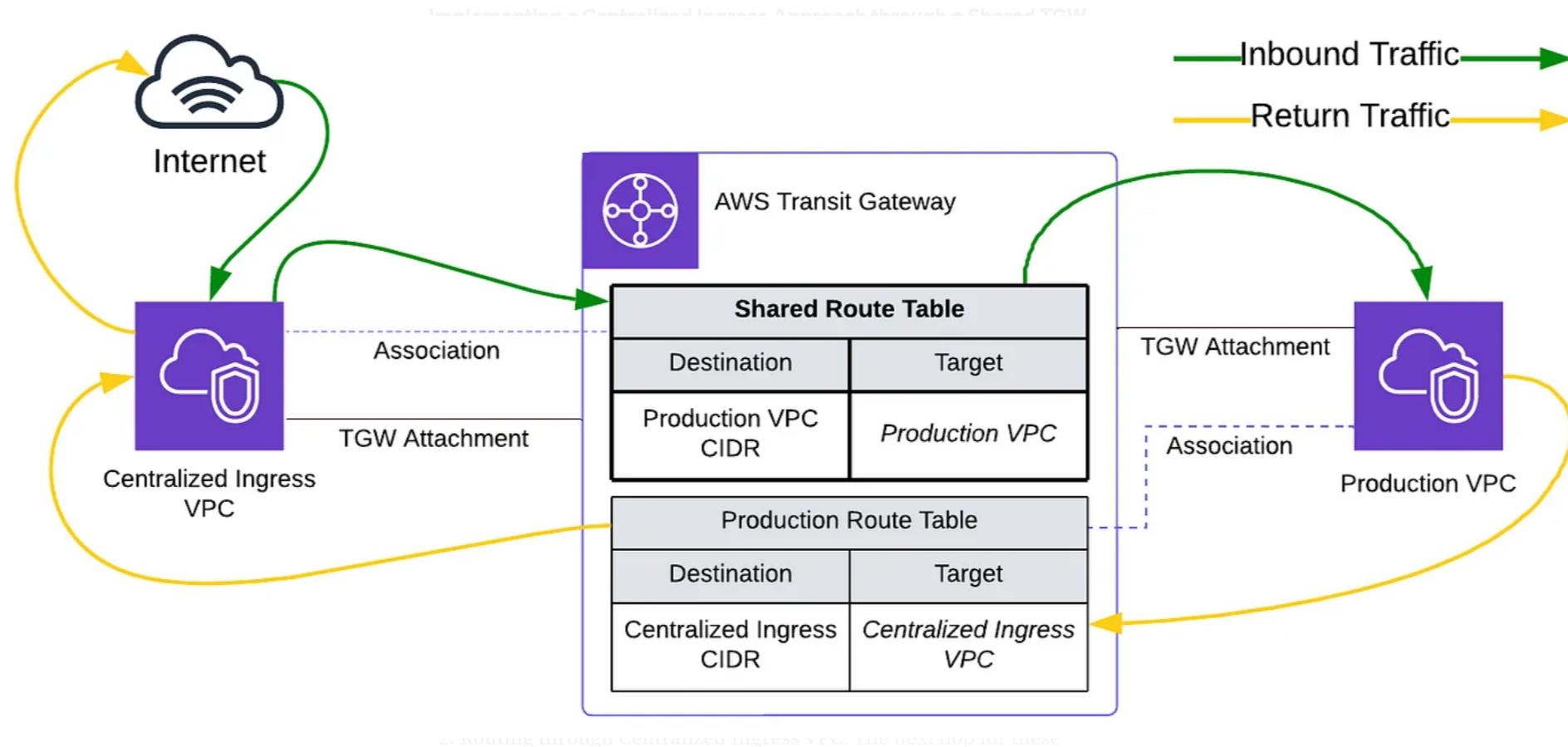 The above diagram provides a comprehensive visual representation of the inbound connectivity traffic flow, starting from the centralized ingress VPC to the Production VPC and back. This flow is enabled by the utilization of meticulously configured route tables, ensuring efficient and secure traffic flow. Here’s a detailed breakdown of how this traffic flow is achieved:
The above diagram provides a comprehensive visual representation of the inbound connectivity traffic flow, starting from the centralized ingress VPC to the Production VPC and back. This flow is enabled by the utilization of meticulously configured route tables, ensuring efficient and secure traffic flow. Here’s a detailed breakdown of how this traffic flow is achieved:
- Internet-Originated Requests: Requests originating from the internet are served by the Application Load Balancer (ALB) located in the centralized ingress VPC. The ALB acts as the entry point for inbound traffic and routes requests to the appropriate workloads using target groups and the path or host-based routing feature.
- Routing through Centralized Ingress VPC: The next hop for these requests is determined by the association of the centralized ingress VPC with the shared transit gateway route table. This association guides traffic toward the correct workload VPCs using the propagated CIDR blocks associated with each Production VPC.
- Serving Traffic to the Production VPC: The traffic is then directed to the intended Production VPC. Here, the workloads are hosted within the VPC process and respond to the incoming requests.
- Return Traffic: As responses are generated by the Production VPC workloads, they are routed back through the centralized ingress VPC to reach the originating clients on the internet. This bidirectional flow is enabled by the shared transit gateway route table, which ensures that responses reach their intended destinations efficiently.
Ensuring Strong On-Premises Connectivity through Site-to-Site VPN
Our solution prioritizes seamless hybrid connectivity to our customer’s data centers by harnessing the capabilities of AWS Site-to-Site VPN and Transit Gateway. This strategic approach centralizes connectivity within the dedicated networking account, acting as the core hub for all hybrid connections. The advantages of adopting this approach are manifold, encompassing consistent throughput, end-to-end encryption, centralized management, and the assurance of secure, high-performance connectivity between our customer’s on-premises facilities. This comprehensive strategy not only ensures efficient data transfer but also upholds the security and reliability of these vital connections.
Streamlined Connectivity to Multiple Data Centers via Transit Gateway VPN Attachments
For the optimal configuration of resources to achieve hybrid connectivity across multiple data centers, our solution leverages Transit Gateway VPN attachments with remarkable efficiency. This approach simplifies the termination of multiple Site-to-Site (S2S) VPN connections from various data centers into a central location, resulting in streamlined monitoring and operational management.
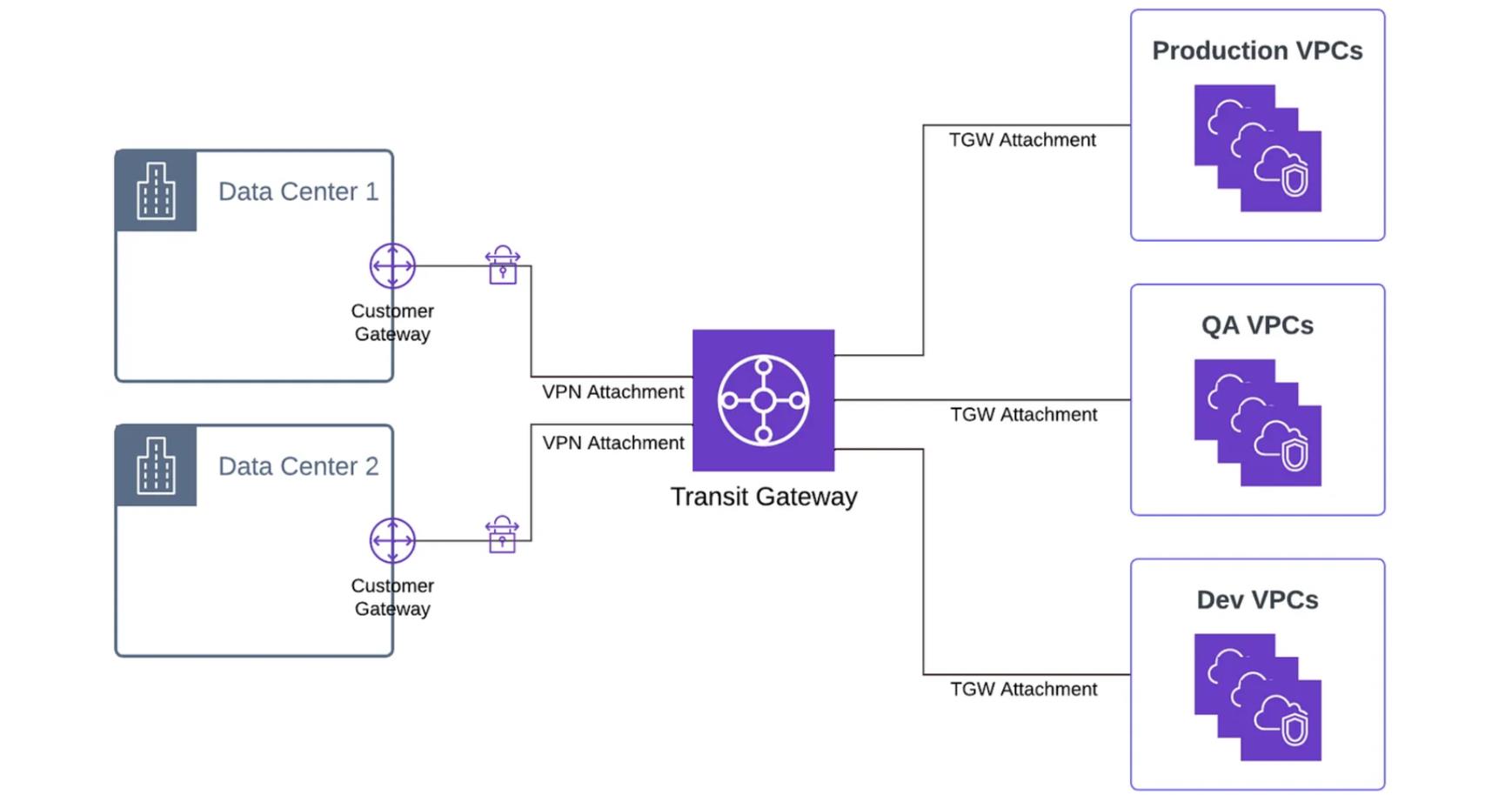
The above diagram offers a visual representation of our hybrid connectivity approach, showcasing how multiple Transit Gateway VPN attachments terminate into the central Transit Gateway. This configuration seamlessly enables our workload VPCs, also interconnected with the Transit Gateway, to communicate effectively with one another. The central Transit Gateway acts as the pivotal hub for these VPN connections, facilitating secure and efficient data exchange between on-premises data centers and AWS cloud resources.
Prioritizing Availability: Implementing Redundant Site-to-Site VPN Connections
Maintaining uninterrupted connectivity to on-premises resources holds the utmost significance, both during the migration process and for everyday operations. To further enhance the reliability and availability of these connections, our solution transcends the standard practice of establishing redundant tunnels for each VPN connection. Instead, it introduces an additional VPN connection to maximize availability and ensure continuous connectivity.
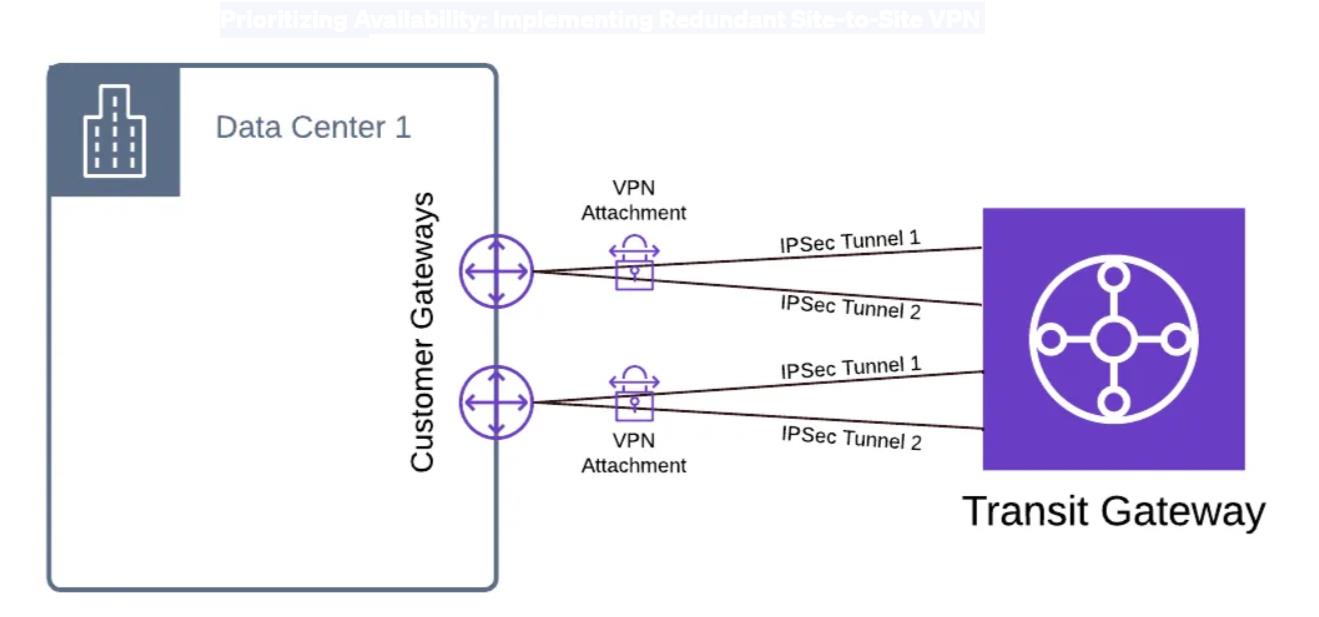 The above diagram illustrates two AWS Site-to-Site VPNs connecting on-premises customer gateway to the AWS Transit Gateway. This proactive approach to redundancy and availability significantly reduces the risk of connectivity disruptions, offering our customer a robust and resilient hybrid connectivity solution. Whether during the migration process or for day-to-day operations, this strategy guarantees that connectivity to on-premises resources remain steadfast and dependable.
The above diagram illustrates two AWS Site-to-Site VPNs connecting on-premises customer gateway to the AWS Transit Gateway. This proactive approach to redundancy and availability significantly reduces the risk of connectivity disruptions, offering our customer a robust and resilient hybrid connectivity solution. Whether during the migration process or for day-to-day operations, this strategy guarantees that connectivity to on-premises resources remain steadfast and dependable.
Implementing the Hybrid Connectivity Approach via a Dynamic TGW Route Table
By leveraging Transit Gateway VPN attachments with dynamic routing configuration, we can effectively propagate on-premises CIDR ranges to the relevant Transit Gateway route tables using Border Gateway Protocol (BGP). This propagation process plays a pivotal role in enabling our customer’s workload VPCs to seamlessly communicate with on-premises resources.
BGP facilitates the automatic exchange of routing information between the on-premises network and the Transit Gateway, ensuring that the appropriate routes are readily available for traffic to traverse between the cloud environment and on-premises infrastructure. This dynamic routing approach optimizes the efficiency and effectiveness of network communication, catering to the organization’s requirements for dependable connectivity between AWS and on-premises resources.
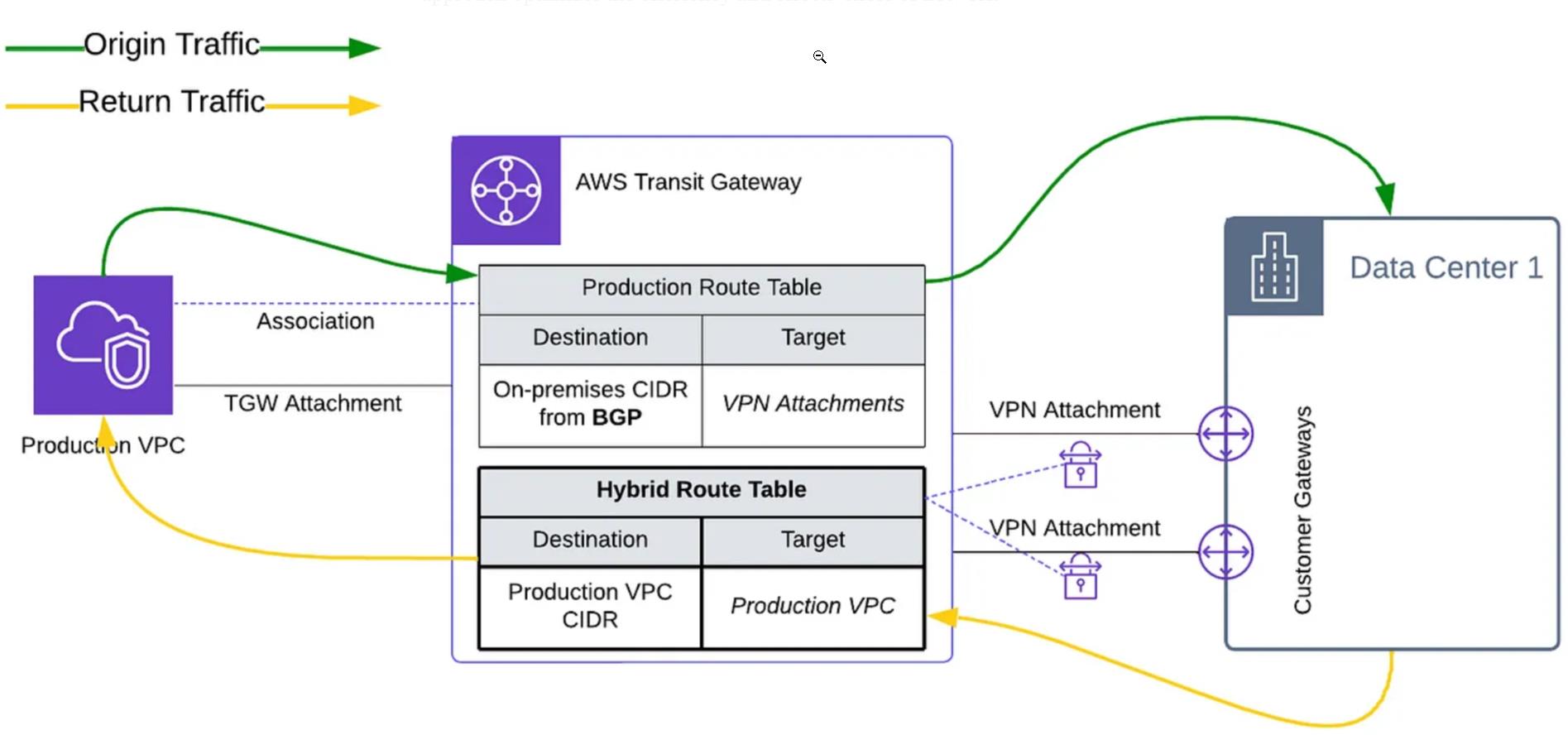
The above diagram presents a comprehensive visual representation of the traffic flow for hybrid connectivity, illustrating how traffic moves between the Production VPC and our on-premises location and back. This smooth flow is made possible through the utilization of meticulously configured route tables, ensuring efficient and secure traffic movement. Here’s a detailed breakdown of how this traffic flow is achieved:
- Traffic Initiation: Workload VPCs, including the Production VPC, initiate traffic destined for the on-premises location. This traffic is directed using specific route tables associated with their respective attachments. Within these route tables, routes propagated via BGP from the on-premises network are present, ensuring precise routing toward the on-premises location.
- Completing the Flow: Return traffic from the on-premises location is directed back to the Production VPC. This is accomplished by associating VPN attachments with the Hybrid Transit Gateway route table. This route table ensures that the CIDRs of the workload VPCs are properly propagated, effectively directing the return traffic.
Through this meticulously structured routing approach, our customer guarantees secure and efficient traffic flow between their AWS cloud environment and on-premises locations, facilitating seamless communication and data exchange.
Enabling Hybrid DNS Resolution via Route53 Resolvers
Based on the requirements identified during the assessment phase, it is imperative for us to achieve reliable DNS resolution between AWS and on-premises environments in both directions. To meet this requirement, our strategy leverages Amazon Route 53 Resolver, capable of responding recursively to DNS queries from AWS resources for public records, VPC-specific DNS names, and records from Route 53 private hosted zones.
This functionality comes pre-enabled in the workload VPCs. However, for comprehensive DNS resolution between AWS and on-premises resources in both directions, resolver endpoints must be configured. The following sections will provide in-depth information on how these resolver endpoints facilitate this critical requirement.
Outbound Resolver Endpoints: Unlocking DNS Resolution to On-Premises
In addition to employing Route 53 resolvers, enabling DNS resolution to our on-premises resources involves using Site-to-Site (S2S) VPN connections to forward DNS queries. To facilitate this, Route 53 outbound resolver endpoints will be configured within multiple availability zones in the centralized egress VPC.
Forwarding rules for specific domains will be established to support the resolution process. These rules will ensure that DNS queries for the designated domains are forwarded via the S2S VPN connections to the on-premises DNS infrastructure, allowing for seamless and reliable DNS resolution between AWS and on-premises resources.
By implementing this configuration, we can achieve efficient DNS resolution while maintaining a secure and interconnected network environment that bridges their AWS and on-premises resources effectively.
Inbound Resolver Endpoints: Ensuring DNS Resolution to AWS
Conversely, to resolve DNS queries from on-premises to AWS, an inbound resolver endpoint needs to be configured. This inbound resolver endpoint will also be deployed in multiple availability zones to ensure reliability and high availability.
The purpose of this inbound resolver endpoint is to provide IP addresses for the on-premises DNS infrastructure to forward DNS queries to. These queries will be directed to the AWS environment via the Site-to-Site (S2S) VPN connection. By establishing this configuration, our customer ensures that DNS queries originating from their on-premises resources can be effectively resolved within the AWS environment, supporting seamless and bi-directional DNS resolution between on-premises and AWS resources.
Our Holistic AWS Networking Strategy in a Nutshell
In the realm of multi-account AWS environments, the need for precision, efficiency, and security is paramount. Our comprehensive networking and connectivity strategy addresses these needs through meticulous planning and a centralized approach.
By optimizing VPC performance, segmenting subnets for enhanced security, and harnessing the power of multiple availability zones, we’ve fortified our customer’s cloud infrastructure. The precision scaling enabled by CIDR allocation and AWS IPAM integration guarantees scalability, while centralized networking simplifies management. The strategic deployment of Transit Gateway and centralized egress and ingress VPCs further streamlines connectivity and enhances security.
As we embark on the cloud journey, this strategy serves as a foundation for efficient, secure, and scalable network and connectivity management. It empowers the organization to navigate the complexities of the cloud with confidence, knowing that their infrastructure is engineered for success.
Moreover, our dependable hybrid connectivity configuration, utilizing AWS Transit Gateway and AWS Site-to-Site VPN, guarantees secure and uninterrupted connections to on-premises resources. This robust setup assures that we can establish and maintain reliable links between our AWS cloud environment and on-premises locations, effectively meeting performance, security, and operational needs.
CONCLUSION
In conclusion, the journey to cloud excellence begins with a comprehensive strategy, and we are well on its way to achieving it. As the digital landscape evolves, this strategy will continue to adapt, ensuring that we remain at the forefront of innovation and security in the ever-changing world of cloud computing.






Add comment