
Website security is a complex topic in today’s times – given the increasing threats and evolving customer expectations. However, by following a systematic approach to website security, you can secure a website from cyberattacks
Why Is Website Security Important?
Website security is essential for several reasons. First, nobody wants a hacked website because leaked user data can cost you your image, as well as business. For example, if your website is hacked and eventually blacklisted, it can lose up to 95 per cent of its organic traffic. Besides, a data breach can also result in lawsuits, substantial fines and loss of reputation.
Not surprisingly, web security is a priority for most businesses. New and advanced technology solutions are being employed to combat website security threats. However, the nature of crime is also evolving in line with developments in security software. Therefore, it is of utmost importance to build a secure site from the start to ensure all data is adequately protected and safe.
Basic Tenets Of Website Security
Security should not be an afterthought. This is demonstrated by the Equifax data breach that impacted the personal information of over 147 million people in 2017. The company only realised about the breach much later and was eventually asked to pay over $700 million in fines to settle the issue.
Before we dive into the basics of website security, here’s a brief of the most common website security threats
- Malware
Virus: It’s the most common type of malware which affects the entire standalone system in the way that an attacker wants. Best way to keep away from a virus is to have an antivirus which is upto date and be cautious with opening a file sent from unknown emails or sms or though any other medium.
Worms: Worms are very dangerous as they affect the entire network once they are injected to any system in the network. The best way to keep away from worms is to have an updated antivirus.
Trojans: This type of malware open the backdoor for other types of malware to access the system - Attacks
DDoS: Distributed Denial of service attack. Here the attacker creates different bots to attack the victim’s machine. Source of the attacker is unknown in this case, although nothing is hidden on the internet.
DrDoS: This is called Distributed reflection Denial of Service attack. In this attack multiple servers are compromised by the attacker which act like the attacking machine to the actual victim. Then the machines which are compromised are doing DDoS to the victims machine.
Man in the middle attack: Let’s say you’re trying to send a confidential file to your boss. Now this file could possibly be tampered, as the name suggests, by a middle man.
This attack can be prevented by hashing the information you’re trying to send.|
Phishing attack: Phishing attack is the most common attack where if successful, there could be a breach of your personal data. The attacker sends in a malicious link, redirecting you to a site that looks similar to the one you use regularly.
So the next time you login to any website, make sure you look at the URL to stay protected. - Spoofing
Web spoofing: In web spoofing, a duplicate of a very trusted site is sent by the
attacker. If the attack is successful, one will end up with their personal details
such as username and password stolen.
IP spoofing: There are sites which authenticate a user based on the IP address.
In this type of attack, the attacker pretends to be you behind a spoofed IP
address to gain access.
DNS spoofing: Also known as DNS cache poisoning. In this attack
the attacker corrupts DNS data that is introduced in the DNS resolver causing
the user to land on the attackers page instead of the trusted page.
What we have shared above is a very broad description of some of the potential security threats. However, the list isn’t comprehensive, and there are hundreds of more threats looming against your website at all times. Having a planned website security framework can help you minimise the danger of being affected by these threats. Even if your website’s security is compromised, a proper security framework can help you mitigate the damage and prevent such happenings in the future.
The US National Institute of Standards and Technology (NIST) has developed a Cybersecurity Framework, which is very helpful in devising a security guide for any firm. It breaks down the website security framework into five parts. Let’s see what each part entails:
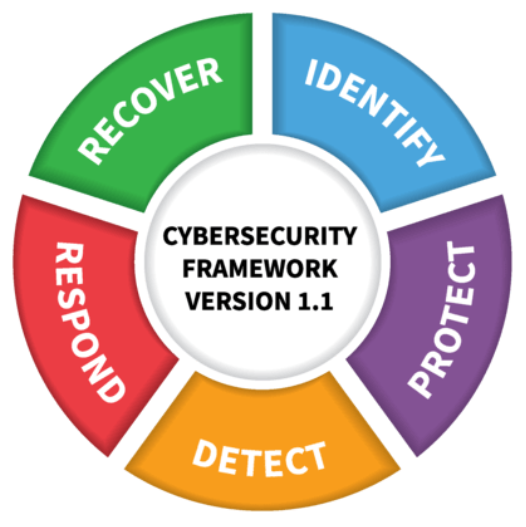
Identify
This is the first stage where all the asset inventory must be documented and reviewed.
This can be broadly divided into the following subcategories that must be reviewed:
- Plugins, extensions, themes, and modules,
- Web properties, servers and infrastructure
- Third-party integrations and services,
- Access points/nodes.
Protect
This is the second and crucial stage where you put preventive measures or layers of defense to safeguard your site. But where do you begin? If you are dealing with an e-commerce site, then you must comply with requirements like PCI DSS or Payment Card Industry Data Security Standard. Besides, it would help if you worked upon environments that are easy to attack. This can be done via security patches that can be regularly updated. You can also activate a web application firewall to block any external attacks. Also, it is a good idea to train your employees and put in place strong access control policies to minimise human error and employee theft.
Detect
Continuous monitoring is pertinent to keep an eye on your site’s security state. It requires you to implement tools for monitoring your website so that you are alerted in case of any issue.
With monitoring, you should be able to verify the state of assets like SSL certificates, DNS records, user access, file integrity, etc. Additionally, scanning software may be implemented to keep a check on your site’s health.
Respond
A response plan is an integral part of any security framework so that you know what to do in case your site’s security is compromised. An incident response plan must include the setting up of an incident response team or person who’d be responsible for reporting the incident. Next, there should be an action plan to mitigate the impact of the event through containment, eradication and recovery.
Recovery
This is the fifth part of the proposed security framework that requires you to take regular back-ups and create recovery options in case your data is lost or crashed.
Now that we have acquainted you with a general framework for website security, here are some proven tips to secure your website:
- Never skip updates, as websites are often compromised due to outdated, insecure software.
- Avoid hosting multiple sites on a single server to prevent the threat of cross-site contamination.
- Limit user access and permissions by granting the minimal privileges on any system, and only for the time the action is necessary.
- Set strong passwords and avoid re-using them.
- Keep control of file permissions to prevent misuse.
- Activate 2FA/MFA wherever possible for an additional layer of authentication
Securing your web assets is crucial for your user experience, brand reputation, as well as your company’s bottom line. Besides investing time and intelligence in creating a reliable security framework, you also need to hire cybersecurity experts for implementing the framework. If you are a software engineer, you can pursue an exciting career in the field of cybersecurity. Sign up on T500 if you are looking for a jump in your career and find suitable opportunities with Fortune 500 firms globally.





Add comment